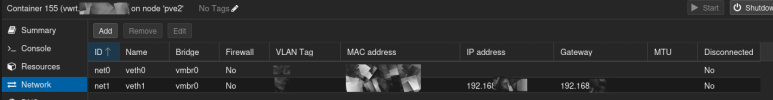
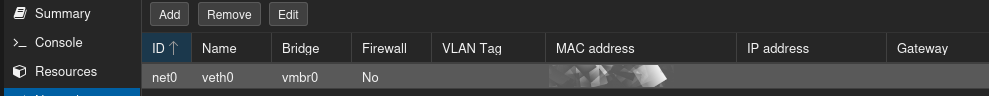
continued here due to character limit
Code:addfile "/etc/openvpn/azire.ca" "600" "root:root" (...)
@shodan. You can use https://gist.github.com to avoid these annoyances.
One example.
As a bonus, it also has the benefit of maintaining a history of revisions, allowing you to track your progress throughout your coding journey.
Keep going with your excellent work in the finest tradition of Holmesian work.