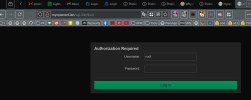
I tried turning off the dhcp server in the openwrt LXC
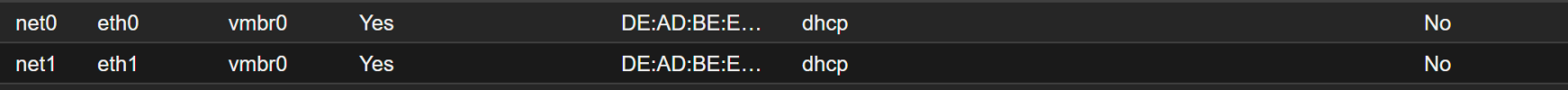
I tried changing the virtual mac address to something else
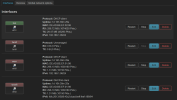
It shows up in my router's dhcp server leases
I ran nmap scan from proxmox host, shows all ports are closed
Seems like something very basic is not working !
Code:
uci set dhcp.lan.ignore='1'
uci commit dhcp
/etc/init.d/dnsmasq restartI tried changing the virtual mac address to something else
It shows up in my router's dhcp server leases
Active DHCP Leases
| Hostname | IPv4 address | MAC address | Lease time remaining | Static Lease |
|---|---|---|---|---|
| openwrt (openwrt.lan) | 192.168.1.136 | DE:AD:BE:EF:01:99 | 11h 59m 51s |
| - | 192.168.1.237 | DE:AD:BE:EF:00:99 | 11h 45m 59s |
I ran nmap scan from proxmox host, shows all ports are closed
Code:
root@proxmox:~/test2# nmap 192.168.1.136
Starting Nmap 7.93 ( https://nmap.org ) at 2024-09-25 07:05 EST
Nmap scan report for 192.168.1.136
Host is up (0.000088s latency).
All 1000 scanned ports on 192.168.1.136 are in ignored states.
Not shown: 1000 closed tcp ports (reset)
MAC Address: DE:AD:BE:EF:01:99 (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 38.64 secondsSeems like something very basic is not working !