Dear all,
My purpose is to set up a Windows Server 2019 VM and using the NVIDIA GPU.
Proxmox 8.1 boots on a ZFS Mirror
My hardware
Motherboard Z590 PRO4
GPU NVIDIA Corporation TU116 [GeForce GTX 1650]
BIOS settings adjustments (listed), ensures that PVE doesn't use my NVIDIA GPU but the motherboard graphics card
in /etc/modprobe.d/kvm.conf
in /etc/default/grub
in /etc/kernel/cmdline
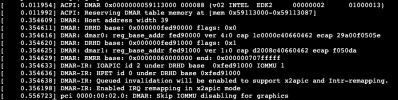
results
in /etc/modules
results
in /etc/modprobe.d/pve-blacklist.conf
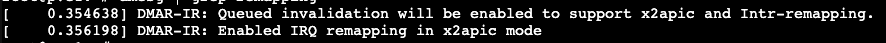
returns

in /etc/modprobe.d/vfio-pci.conf
Final result is that I'm still getting the following yellow message : No IOMMU detected, please activate it.See Documentation for further information. in the proxmox UI.
I'm totally stuck and have been browsing the internet to find any kind of clue how to solve this, without luck. Can someone put me on the right track ?
My purpose is to set up a Windows Server 2019 VM and using the NVIDIA GPU.
Proxmox 8.1 boots on a ZFS Mirror
My hardware
Motherboard Z590 PRO4
GPU NVIDIA Corporation TU116 [GeForce GTX 1650]
BIOS settings adjustments (listed), ensures that PVE doesn't use my NVIDIA GPU but the motherboard graphics card
- Primary Graphic Adapter set to onboard
- Enable VT-d
- Enable SR-IOV
- Set PEG {NUMBER} ASPM L0sL1
- Enable 4G decoding
- CAM disabled
- IGPU Enabled
- Disable CSM/Legacy Boot
in /etc/modprobe.d/kvm.conf
Code:
options kvm ignore_msrs=Y report_ignored_msrs=0
Code:
GRUB_CMDLINE_LINUX_DEFAULT="quiet intel_iommu=on iommu=pt initcall_blacklist=sysfb_init pcie_acs_override=downstream,multifunction"in /etc/kernel/cmdline
Code:
root=ZFS=rpool/ROOT/pve-1 boot=zfs intel_iommu=on iommu=pt initcall_blacklist=sysfb_init pcie_acs_override=downstream,multifunction
Code:
update-grub
pve-efiboot-tool refresh
reboot
Code:
dmesg | grep -e DMAR -e IOMMU
in /etc/modules
Code:
vfio
vfio_iommu_type1
vfio_pci
Code:
update-initramfs -u -k all
Code:
dmesg | grep remappingin /etc/modprobe.d/pve-blacklist.conf
Code:
blacklist nouveau
blacklist nvidia
blacklist nvidiafb
blacklist snd_hda_codec_hdmi
blacklist snd_hda_intel
blacklist snd_hda_codec
blacklist snd_hda_core
blacklist radeon
blacklist amdgpu
Code:
pvesh get /nodes/pve1/hardware/pci --pci-class-blacklist ""
in /etc/modprobe.d/vfio-pci.conf
Code:
options vfio-pci ids=10de:2188 disable_vga=1Final result is that I'm still getting the following yellow message : No IOMMU detected, please activate it.See Documentation for further information. in the proxmox UI.
I'm totally stuck and have been browsing the internet to find any kind of clue how to solve this, without luck. Can someone put me on the right track ?

