Hi,
I want to setup a Proxmox instance, so that it is accessable via a public domain, by going to https://pve.domain.com, logging in and using it, as you would do it under it's local IP e.g. https://10.0.1.2:8006.
One special thing to mention, is that between my Router (port forwarding) and the Proxmox Server there's an Apache Webserver, serving as a proxy for different domain names, by routing the domains to the corresponding IPs and Ports.
In this case:
WWW -> Router : Port443 -> ReverseProxy : vHost,pve.domain.com -> Proxmox Server (https://10.0.1.2:8006)
Enough theory. So what I actually did was:
1.) On my registrars website I setup a DNS record for pve.domain.com pointing to my public IP
2.) On the Router I setup port forwarding for port 80 and 443 to my Proxy Server
3.) On the Proxy Server I setup a Reverse Proxy for pve.domain.com to redirect to the Proxmox WebUI, and created a Let's Encrypt SSL certificate:
Output:
Virtual Host:
That's it, I thought. At least that's the way I've done it on every other service till now.
Going to https://pve.domain.com establishes an ecrypted connection (Verified by: Let's Encrypt | view Certificate)
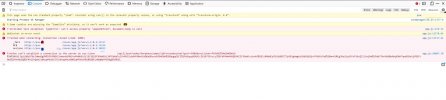
Logging into the Proxmox WebUI works too, and all the site-content is loaded susccsessfully:
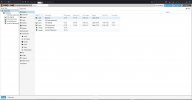
But the problem I have, is that I can't open a single console inside the WebUI. Neither the console of the host (name: Morpheus; error: "undefinded (code: 1006)") nor those of the VMs (no matter wether noVNC or xterm.js).
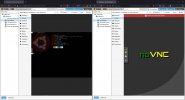
Going to https://10.0.1.2:8006 and opening the consoles at the exact same time works perfectly fine:
I highly suspect, that this is a security mechanism and has something to do with the Proxmox self-signed certificate and therefore the browser warning when you go to https://10.0.1.2:8006, that I've bypassed with my solution:

I tried solving this issue today, but I had no success, whatsoever. What is the exact reason for this issue and what suggestions do you have for solving it?
I want to setup a Proxmox instance, so that it is accessable via a public domain, by going to https://pve.domain.com, logging in and using it, as you would do it under it's local IP e.g. https://10.0.1.2:8006.
One special thing to mention, is that between my Router (port forwarding) and the Proxmox Server there's an Apache Webserver, serving as a proxy for different domain names, by routing the domains to the corresponding IPs and Ports.
In this case:
WWW -> Router : Port443 -> ReverseProxy : vHost,pve.domain.com -> Proxmox Server (https://10.0.1.2:8006)
Enough theory. So what I actually did was:
1.) On my registrars website I setup a DNS record for pve.domain.com pointing to my public IP
2.) On the Router I setup port forwarding for port 80 and 443 to my Proxy Server
3.) On the Proxy Server I setup a Reverse Proxy for pve.domain.com to redirect to the Proxmox WebUI, and created a Let's Encrypt SSL certificate:
Code:
sudo vi /etc/apache2/sites-available/pve.domain.com.conf
sudo a2enmod proxy_http ssl
sudo a2ensite pve.domain.com
sudo systemctl restart apache2
Code:
sudo certbot --apache --agree-tos --redirect --register-unsafely-without-email --hsts -d pve.domain.com
Code:
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Congratulations! You have successfully enabled https://pve.domain.com
You should test your configuration at:
https://www.ssllabs.com/ssltest/analyze.html?d=pve.domain.com
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -Virtual Host:
Code:
<VirtualHost *:80>
ServerName pve.domain.com
CustomLog ${APACHE_LOG_DIR}/access.log combined
ErrorLog ${APACHE_LOG_DIR}/error.log
ProxyPass / http://10.0.1.2:80/
ProxyPassReverse / http://10.0.1.2:80/
</VirtualHost>
<VirtualHost *:443>
ServerName pve.domain.com
CustomLog ${APACHE_LOG_DIR}/access.log combined
ErrorLog ${APACHE_LOG_DIR}/error.log
ProxyPass / https://10.0.1.2:8006/
ProxyPassReverse / https://10.0.1.2:8006/
SSLProxyCheckPeerCN off
SSLProxyCheckPeerExpire off
SSLProxyCheckPeerName off
SSLProxyEngine on
SSLProxyVerify none
SSLCertificateFile /etc/letsencrypt/live/pve.domain.com/fullchain.pem
SSLCertificateKeyFile /etc/letsencrypt/live/pve.domain.com/privkey.pem
Include /etc/letsencrypt/options-ssl-apache.conf
Header always set Strict-Transport-Security "max-age=31536000"
</VirtualHost>That's it, I thought. At least that's the way I've done it on every other service till now.
Going to https://pve.domain.com establishes an ecrypted connection (Verified by: Let's Encrypt | view Certificate)
Logging into the Proxmox WebUI works too, and all the site-content is loaded susccsessfully:

But the problem I have, is that I can't open a single console inside the WebUI. Neither the console of the host (name: Morpheus; error: "undefinded (code: 1006)") nor those of the VMs (no matter wether noVNC or xterm.js).
Going to https://10.0.1.2:8006 and opening the consoles at the exact same time works perfectly fine:

I highly suspect, that this is a security mechanism and has something to do with the Proxmox self-signed certificate and therefore the browser warning when you go to https://10.0.1.2:8006, that I've bypassed with my solution:

I tried solving this issue today, but I had no success, whatsoever. What is the exact reason for this issue and what suggestions do you have for solving it?
Last edited: