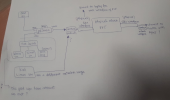
So this is how I thought of it so far.. (I am a beginner)
Questions:
1. The way I wanna get internet is not right. How else? Add another pfsense vm for vmbr1 iface(=gb2 physical) and so the internet passes through it first?
2. For vmbr0: I want to split it in2 : one part for the Dmz-style network; another for the Linux vm. Can I config it so that the DMZ vm gets internet, and also the Kali vm?
Also, does that dmz vm need internet at all, if I am supposed to add some type of public-facing server on it (like dns/ email)? And the LAN part is supposed to not have internet at all?
3. The Win 2019 in the LAN part, is supposed to manage the other win10 vms, but it is unsafe to keep it on the same network, right? But if I create a separate vlan for it, then it will no longer be able to connect to/ manage users, computers from the win10 vms?
4. I feel like what I am trying to do with the gb2 if, aka vmbr1 is totally wrong and not secure, like
sb-jw says, but I don't have any other idea.
(I am thinking that interface gb1 is already occupied, because that is how I am accessing the web interface, connecting the server to my laptop. And then, I could use the other gb2 iface, and assign it vmbr1 virtual, so that the ethernet with internet comes that way into the server and can be managed by my pfsense firewall..). I also read that there is the option to enable some firewall from the PVE web interface.. could I use this one?
5. Any other idea of how to better manage/ split the server's interfaces? Or the virtual bridges, for that matter?
6. How to create the virtual switch?
Answer to any question would be much appreciated!


