Hello,
I would like to connect the Hetzner Cloud Network with an SDN EVPN zone defined in Proxmox.
What do I have:
And my question is how to do it? What am I missing in routing?
Infos:
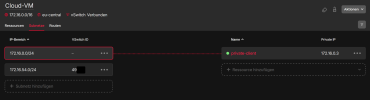
Network Hetzner Side:
Hetzner Cloud 172.16.0.0/16
Subnetz Cloudserver 172.16.0.0/24
Subnetz vSwitch 172.16.54.0/24
(see attached Picture)
Network Proxmox Cluster:
VXLAN: 172.16.54.0/24
Network inside EVPN:
VMs: 192.168.13.0/24
some configs:
SDN:
I would like to connect the Hetzner Cloud Network with an SDN EVPN zone defined in Proxmox.
What do I have:
- Hetzner Cloud Network with Cloudserver.
- Proxmox 3-node cluster (Ceph, HA, EVPN)
- functioning vSwitch
- the dedicated servers (ProxmoxCluster) are connected to the vSwitch.
- Hetzner Cloud network is connected to the vSwitch
- ping between the VMs within the Proxmox cluster, regardless of the node on which the VM is located.
- ping between the Hetzner cloud servers
- ping between the Hetzner cloud servers and the Proxmox hosts (works in both directions)
- ping VMs from proxmox-host that host the VM
- ping from a Hetzner Cloudserver to a VM inside the EVPN on a proxmox host.
- ping a VM on other proxmox host hosted. (ping from pve2 -> pve3.vm1)
And my question is how to do it? What am I missing in routing?
Infos:
Network Hetzner Side:
Hetzner Cloud 172.16.0.0/16
Subnetz Cloudserver 172.16.0.0/24
Subnetz vSwitch 172.16.54.0/24
(see attached Picture)
Network Proxmox Cluster:
VXLAN: 172.16.54.0/24
Network inside EVPN:
VMs: 192.168.13.0/24
some configs:
Bash:
root@pve2 ~ #cat /etc/network/interfaces
auto lo
iface lo inet loopback
iface lo inet6 loopback
iface enp5s0 inet manual
auto enp5s0.4050
iface enp5s0.4050 inet static
address 172.16.50.2/24
mtu 1400
#Hetzner VSwitch (Cluster-Corosync)
auto enp5s0.4051
iface enp5s0.4051 inet static
address 172.16.51.2/24
mtu 1400
#Hetzner VSwitch (Cluster-Migration)
auto enp5s0.4052
iface enp5s0.4052 inet static
address 172.16.52.2/24
mtu 1400
#Hetzner VSwitch (Ceph-Public)
auto enp5s0.4053
iface enp5s0.4053 inet static
address 172.16.53.2/24
mtu 1400
#Hetzner VSwitch (Ceph-ClusterNetwork)
auto enp5s0.4054
iface enp5s0.4054 inet static
address 172.16.54.2/24
vlan-raw-device enp5s0
mtu 1400
post-up ip route add 172.16.0.0/24 via 172.16.54.1 dev enp5s0.4054
down ip route del 172.16.0.0/24
#Hetzner VSwitch (Client VxLAN)
auto vmbr0
iface vmbr0 inet static
address 167.235.1.97/26
gateway 167.235.1.65
bridge-ports enp5s0
bridge-stp off
bridge-fd 1
bridge-vlan-aware yes
bridge-vids 2-4094
hwaddress a8:a1:59:15:a7:4b
pointopoint 167.235.1.65
up sysctl -p
auto vmbr1
iface vmbr1 inet static
address 172.17.1.1/24
bridge-ports none
bridge-stp off
bridge-fd 0
post-up iptables -t nat -A POSTROUTING -s '172.17.1.1/24' -o vmbr0 -j MASQUERADE
post-down iptables -t nat -D POSTROUTING -s '172.17.1.1/24' -o vmbr0 -j MASQUERADE
#NAT
source /etc/network/interfaces.d/*SDN:
Bash:
root@pve2 ~ # cat /etc/network/interfaces.d/sdn
#version:109
auto prodvpn
iface prodvpn
address 192.168.13.1/24
post-up iptables -t nat -A POSTROUTING -s '192.168.13.0/24' -o vmbr0 -j SNAT --to-source 167.235.1.97
post-down iptables -t nat -D POSTROUTING -s '192.168.13.0/24' -o vmbr0 -j SNAT --to-source 167.235.1.97
post-up iptables -t raw -I PREROUTING -i fwbr+ -j CT --zone 1
post-down iptables -t raw -D PREROUTING -i fwbr+ -j CT --zone 1
hwaddress BC:24:11:CA:E5:34
bridge_ports vxlan_prodvpn
bridge_stp off
bridge_fd 0
mtu 1346
alias mein_prod_alias
ip-forward on
arp-accept on
vrf vrf_evpnzone
auto vrf_evpnzone
iface vrf_evpnzone
vrf-table auto
post-up ip route del vrf vrf_evpnzone unreachable default metric 4278198272
auto vrfbr_evpnzone
iface vrfbr_evpnzone
bridge-ports vrfvx_evpnzone
bridge_stp off
bridge_fd 0
mtu 1346
vrf vrf_evpnzone
auto vrfvx_evpnzone
iface vrfvx_evpnzone
vxlan-id 10000
vxlan-local-tunnelip 172.16.54.2
bridge-learning off
mtu 1346
auto vxlan_prodvpn
iface vxlan_prodvpn
vxlan-id 100002
vxlan-local-tunnelip 172.16.54.2
bridge-learning off
mtu 1346