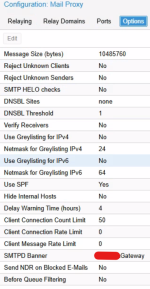
Dear Stoiko,
thank you for your response. I went ahead and tried that out again. I hope I got the requested info right:
1. I sent a test message and got the log via Putty at var/log > mail.log
2025-10-27T10:02:23.666164+01:00 gf-mlgw-01 pmgpolicy[746]: starting policy database maintenance (greylist, rbl)
2025-10-27T10:02:23.726348+01:00 gf-mlgw-01 pmgpolicy[746]: end policy database maintenance (20 ms, 3 ms)
2025-10-27T10:02:41.697924+01:00 gf-mlgw-01 pmg-smtp-filter[745]: starting database maintenance
2025-10-27T10:02:41.713983+01:00 gf-mlgw-01 pmg-smtp-filter[745]: end database maintenance (16 ms)
2025-10-27T10:02:43.125797+01:00 gf-mlgw-01 postfix/smtpd[36527]: connect from VM1.domain1.com[172.30.13.1]
2025-10-27T10:02:46.579946+01:00 gf-mlgw-01 postfix/smtpd[36527]: 8D556100A7F: client=VM1.domain1.com[172.30.13.1]
2025-10-27T10:02:48.841160+01:00 gf-mlgw-01 postfix/cleanup[36530]: 8D556100A7F: message-id=<>
2025-10-27T10:02:48.844755+01:00 gf-mlgw-01 postfix/qmgr[742]: 8D556100A7F: from=<
user1@domain1.com>, size=461, nrcpt=1 (queue active)
2025-10-27T10:02:48.904116+01:00 gf-mlgw-01 pmg-smtp-filter[25730]: 2025/10/27-10:02:48 CONNECT TCP Peer: "[127.0.0.1]:36244" Local: "[127.0.0.1]:10023"
2025-10-27T10:02:48.949279+01:00 gf-mlgw-01 pmg-smtp-filter[25730]: 100BDD68FF3538E6B52: new mail message-id=
2025-10-27T10:02:48.986494+01:00 gf-mlgw-01 postfix/smtpd[36535]: connect from localhost.localdomain[127.0.0.1]
2025-10-27T10:02:48.988847+01:00 gf-mlgw-01 postfix/smtpd[36535]: F160B100BDF: client=localhost.localdomain[127.0.0.1], orig_client=VM1.domain1.com[172.30.13.1]
2025-10-27T10:02:49.031541+01:00 gf-mlgw-01 postfix/cleanup[36530]: F160B100BDF: message-id=<
20251027090248.F160B100BDF@gf-mlgw-01.domain1.com>
2025-10-27T10:02:49.042796+01:00 gf-mlgw-01 postfix/qmgr[742]: F160B100BDF: from=<
user1@domain1.com>, size=772, nrcpt=1 (queue active)
2025-10-27T10:02:49.043068+01:00 gf-mlgw-01 postfix/smtpd[36535]: disconnect from localhost.localdomain[127.0.0.1] ehlo=1 xforward=1 mail=1 rcpt=1 data=1 commands=5
2025-10-27T10:02:49.043807+01:00 gf-mlgw-01 pmg-smtp-filter[25730]: 100BDD68FF3538E6B52: accept mail to <
user2@domain2.de> (F160B100BDF) (rule: default-accept)
2025-10-27T10:02:49.049028+01:00 gf-mlgw-01 pmg-smtp-filter[25730]: 100BDD68FF3538E6B52: processing time: 0.099 seconds (0, 0.027, 0)
2025-10-27T10:02:49.050114+01:00 gf-mlgw-01 postfix/lmtp[36531]: 8D556100A7F: to=<
user2@domain2.de>, relay=127.0.0.1[127.0.0.1]:10023, delay=3.1, delays=2.9/0.06/0.04/0.1, dsn=2.5.0, status=sent (250 2.5.0 OK (100BDD68FF3538E6B52))
2025-10-27T10:02:49.050432+01:00 gf-mlgw-01 postfix/qmgr[742]: 8D556100A7F: removed
2025-10-27T10:02:49.266694+01:00 gf-mlgw-01 postfix/smtp[36536]: SSL_connect error to mx00.ionos.de[212.227.15.41]:25: -1
2025-10-27T10:02:49.267084+01:00 gf-mlgw-01 postfix/smtp[36536]: warning: TLS library problem: error:0A0003E8:SSL routines::reason(1000):../ssl/record/rec_layer_s3.c:1605:SSL alert number 0:
2025-10-27T10:02:49.267243+01:00 gf-mlgw-01 postfix/smtp[36536]: F160B100BDF: Cannot start TLS: handshake failure
2025-10-27T10:02:49.394720+01:00 gf-mlgw-01 postfix/smtp[36536]: SSL_connect error to mx01.ionos.de[217.72.192.67]:25: -1
2025-10-27T10:02:49.394878+01:00 gf-mlgw-01 postfix/smtp[36536]: warning: TLS library problem: error:0A0003E8:SSL routines::reason(1000):../ssl/record/rec_layer_s3.c:1605:SSL alert number 0:
2025-10-27T10:02:49.405889+01:00 gf-mlgw-01 postfix/smtp[36536]: F160B100BDF: to=<
user2@domain2.de>, relay=mx01.ionos.de[217.72.192.67]:25, delay=0.41, delays=0.05/0.06/0.29/0, dsn=4.7.5, status=deferred (Cannot start TLS: handshake failure)
2025-10-27T10:02:49.724689+01:00 gf-mlgw-01 postfix/smtpd[36527]: disconnect from VM1.domain1.com[172.30.13.1] helo=0/1 ehlo=0/1 mail=1 rcpt=1 data=1 quit=1 commands=4/6
2025-10-27T10:04:33.860557+01:00 gf-mlgw-01 pmgpolicy[746]: starting policy database maintenance (greylist, rbl)
2025-10-27T10:04:33.896880+01:00 gf-mlgw-01 pmgpolicy[746]: end policy database maintenance (23 ms, 4 ms)
2025-10-27T10:04:49.172256+01:00 gf-mlgw-01 pmg-smtp-filter[745]: starting database maintenance
2025-10-27T10:04:49.207660+01:00 gf-mlgw-01 pmg-smtp-filter[745]: end database maintenance (35 ms)
2. I tested the command you gave on the PMG via Putty against two IONOS Mail servers
root@gf-mlgw-01:/var/log# openssl s_client -connect
mx00.ionos.de:25 -starttls smtp
CONNECTED(00000003)
depth=2 C = DE, O = T-Systems Enterprise Services GmbH, OU = T-Systems Trust Center, CN = T-TeleSec GlobalRoot Class 2
verify return:1
depth=1 C = DE, O = Deutsche Telekom Security GmbH, CN = Telekom Security ServerID OV Class 2 CA
verify return:1
depth=0 C = DE, ST = Rheinland-Pfalz, L = Montabaur, O = IONOS SE, CN =
mx.kundenserver.de
verify return:1
---
Certificate chain
0 s:C = DE, ST = Rheinland-Pfalz, L = Montabaur, O = IONOS SE, CN =
mx.kundenserver.de
i:C = DE, O = Deutsche Telekom Security GmbH, CN = Telekom Security ServerID OV Class 2 CA
a

KEY: rsaEncryption, 3072 (bit); sigalg: RSA-SHA256
v:NotBefore: Apr 10 06:20:33 2025 GMT; NotAfter: Apr 14 23:59:59 2026 GMT
1 s:C = DE, O = Deutsche Telekom Security GmbH, CN = Telekom Security ServerID OV Class 2 CA
i:C = DE, O = T-Systems Enterprise Services GmbH, OU = T-Systems Trust Center, CN = T-TeleSec GlobalRoot Class 2
a

KEY: rsaEncryption, 3072 (bit); sigalg: RSA-SHA256
v:NotBefore: Aug 2 09:16:44 2022 GMT; NotAfter: Aug 2 23:59:59 2027 GMT
---
Server certificate
-----BEGIN CERTIFICATE-----
MIIJyzCCCDOgAwIBAgIQJ+/Vt7F2EOSuhtQN6pea1zANBgkqhkiG9w0BAQsFADBo
MQswCQYDVQQGEwJERTEnMCUGA1UECgweRGV1dHNjaGUgVGVsZWtvbSBTZWN1cml0
eSBHbWJIMTAwLgYDVQQDDCdUZWxla29tIFNlY3VyaXR5IFNlcnZlcklEIE9WIENs
YXNzIDIgQ0EwHhcNMjUwNDEwMDYyMDMzWhcNMjYwNDE0MjM1OTU5WjBrMQswCQYD
VQQGEwJERTEYMBYGA1UECBMPUmhlaW5sYW5kLVBmYWx6MRIwEAYDVQQHEwlNb250
YWJhdXIxETAPBgNVBAoTCElPTk9TIFNFMRswGQYDVQQDExJteC5rdW5kZW5zZXJ2
ZXIuZGUwggGiMA0GCSqGSIb3DQEBAQUAA4IBjwAwggGKAoIBgQC1HupYZ4y0eVu5
ASg9bYz/VM6K3SNSBqtVpjFyOw5epjU5O1q5NIF75UzamF7TKoEpwFIHU9z2X59O
47sya+FHdY+amLQPAOQh7AMQ84JaRS4xLg5D3/hPMmL0U9c/Gd7JsMsMV8+RW6hX
CCf4vVuYiErNlfsl2XWuVlnqsopLLGZY9QVyHlpeTwmlVVQn2auwNI7MMt9BlP8T
iM8MA8fqzt1BWQfroDtrUKkN5snhmrSO8zbjQEDSFkj1BkX4pY06KmzbrWV2SKaS
q5H/jbgL84A1qVRX8qyZL9wFUwP9fSGT/d7XGJdnrFaOov7cwOKOzeJ0Nn2sP4NI
IggMFm8VC3/qQ+5qePfGLYhHm0D/mNTyhYSct9o8A4iNsmJPYM/lN12EHxMfp3Gm
1J4YWLfyDyLg/2vGQ6dUxBtCYNLkAiBbcYbB0COTDbne3U+94ePHFoOCJ+hO2OYe
uD40N5vkHPQJOKvH0EYOT5MYnk4QDlU5O1dQvOuMU2e/qtYL2ycCAwEAAaOCBWww
ggVoMB8GA1UdIwQYMBaAFBwFk7F/qDQwjFLglkCgcqMQXeD/MA4GA1UdDwEB/wQE
AwIFoDAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYBBQUHAwEwHQYDVR0OBBYEFAHa
cm3+JjncStz2NF24ZIUS/GmNMFMGA1UdIARMMEowSAYGZ4EMAQICMD4wPAYIKwYB
BQUHAgEWMGh0dHA6Ly9kb2NzLnNlcnZlcmlkLnRlbGVzZWMuZGUvY3BzL3NlcnZl
cmlkLmh0bTBeBgNVHR8EVzBVMFOgUaBPhk1odHRwOi8vY3JsLnNlcnZlcmlkLnRl
bGVzZWMuZGUvcmwvVGVsZWtvbV9TZWN1cml0eV9TZXJ2ZXJJRF9PVl9DbGFzc18y
X0NBLmNybDCBnwYIKwYBBQUHAQEEgZIwgY8wMQYIKwYBBQUHMAGGJWh0dHA6Ly9v
Y3NwLnNlcnZlcmlkLnRlbGVzZWMuZGUvb2NzcHIwWgYIKwYBBQUHMAKGTmh0dHA6
Ly9jcnQuc2VydmVyaWQudGVsZXNlYy5kZS9jcnQvVGVsZWtvbV9TZWN1cml0eV9T
ZXJ2ZXJJRF9PVl9DbGFzc18yX0NBLmNydDAMBgNVHRMBAf8EAjAAMIIBHwYDVR0R
BIIBFjCCARKCEm14Lmt1bmRlbnNlcnZlci5kZYIUbXgwMC5rdW5kZW5zZXJ2ZXIu
ZGWCFG14MDEua3VuZGVuc2VydmVyLmRlghlteDAwLmVtaWcua3VuZGVuc2VydmVy
LmRlghlteDAxLmVtaWcua3VuZGVuc2VydmVyLmRlghBteDAwLmlvbm9zLmNvLnVr
gg1teDAwLmlvbm9zLmRlgg1teDAwLmlvbm9zLmVzgg1teDAwLmlvbm9zLmZygg1t
eDAwLmlvbm9zLml0ghBteDAxLmlvbm9zLmNvLnVrgg1teDAxLmlvbm9zLmRlgg1t
eDAxLmlvbm9zLmVzgg1teDAxLmlvbm9zLmZygg1teDAxLmlvbm9zLml0MIICbQYK
KwYBBAHWeQIEAgSCAl0EggJZAlcAdQAOV5S8866pPjMbLJkHs/eQ35vCPXEyJd0h
qSWsYcVOIQAAAZYeW4HFAAAEAwBGMEQCIBLymA1J/70UBWSsPfPhXuDn/iIASoPT
ueZoXRk5UojQAiAK8NEXRRzcVO4cvVqbEoxvMIucz4Demoo0IhKmuAFQdQB1AJaX
ZL9VWJet90OHaDcIQnfp8DrV9qTzNm5GpD8PyqnGAAABlh5bgVoAAAQDAEYwRAIg
MD1yhm+NKcS63RnOz+wyTLsIG6u0rvJIl3jGrgXyN34CIGau5ApSaet/jn77C6Lc
FV2BCUHVVCJaaktEWPUQWxLPAHcAGYbUxyiqb/66A294Kk0BkarOLXIxD67OXXBB
LSVMx9QAAAGWHluDYwAABAMASDBGAiEA9rAJvCjzYk23FUf0+VtTI6IpYrT9uRZM
NDvaLzAuSWUCIQCvqV0dxkM+DWVj5NVTy3Zp+fFT4LJ1p4n0mLdWTrGxkQB2AEmc
m2neHXzs/DbezYdkprhbrwqHgBnRVVL76esp3fjDAAABlh5bgW4AAAQDAEcwRQIh
AMaoYcuKotRbQL8R4LvPJZUyqW4BIrF26rimIRsnVciUAiBgJBf7yfZ/IA6yWyt3
BdyVaL9KsNbSJ2B2ApWBNXHM7gB2AGQRxGykEuyniRyiAi4AvKtPKAfUHjUnq+r+
1QPJfc3wAAABlh5bgg4AAAQDAEcwRQIhAIH7CD4stu90ZH3TYKDB/Ue6+aOp29T+
jwOiNh8ztlu0AiARN2Id6gq8tPqcOPa2+OclKaYdxtC4L48nYTugbyhKNTANBgkq
hkiG9w0BAQsFAAOCAYEAKUrbKE1yoO5OoS029PPZLvKBdhT46gXLO8hd5Id0wpSb
3U4IR99E+r1ocVxvpIczjLRzaQx4K0K1vzHQK5HBlmaC7e2NhBHacYl1hO9SnBBh
JtvjOgha8cAt+Q5B7Y1VCz/xkXaUyPUl6BpAxTQa7NWTv8LBDaica3t4a0bBRMAX
NLirc7dOv/l+8h+uNUuHJYGoRWuGSkDH8qV6I0AOSoNlY9Y0Dkw7JEuif/zT5+L2
ZpuAq4ha3Q7BPlmUSXj335Sxl2lgqc8O9zQuZhpNVs+OHRPw0pLGLOGM6mDDmEKM
yFnom/au0Il9dI950sWgx4KoajtxSt2p7MWxa2XtQ+HN1xPwg4J1LHqzUi+0Pwk0
q7kvwrDYYPQQCLZAAXbdaIu62jGwqvk/nUNdyGKQzpiLSA10tuARzZJS/Y0xLpYb
SDFlK5wCD9y/4aDWyRi33Y/hBPm7Os2PTZweRtbNUn10XipNcZ2tgJtDOt8J4YUH
Gpz0PL4AdC+HeB6WXN2h
-----END CERTIFICATE-----
subject=C = DE, ST = Rheinland-Pfalz, L = Montabaur, O = IONOS SE, CN =
mx.kundenserver.de
issuer=C = DE, O = Deutsche Telekom Security GmbH, CN = Telekom Security ServerID OV Class 2 CA
---
No client certificate CA names sent
Peer signing digest: SHA256
Peer signature type: RSA-PSS
Server Temp Key: ECDH, prime256v1, 256 bits
---
SSL handshake has read 4905 bytes and written 784 bytes
Verification: OK
---
New, TLSv1.3, Cipher is TLS_AES_256_GCM_SHA384
Server public key is 3072 bit
Secure Renegotiation IS NOT supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
Early data was not sent
Verify return code: 0 (ok)
---
250 STARTTLS
421
kundenserver.de Service closing transmission channel - command timeout
closed
root@gf-mlgw-01:/var/log#
root@gf-mlgw-01:/var/log#
root@gf-mlgw-01:/var/log# openssl s_client -connect
mx01.ionos.de:25 -starttls smtp
CONNECTED(00000003)
depth=2 C = DE, O = T-Systems Enterprise Services GmbH, OU = T-Systems Trust Center, CN = T-TeleSec GlobalRoot Class 2
verify return:1
depth=1 C = DE, O = Deutsche Telekom Security GmbH, CN = Telekom Security ServerID OV Class 2 CA
verify return:1
depth=0 C = DE, ST = Rheinland-Pfalz, L = Montabaur, O = IONOS SE, CN =
mx.kundenserver.de
verify return:1
---
Certificate chain
0 s:C = DE, ST = Rheinland-Pfalz, L = Montabaur, O = IONOS SE, CN =
mx.kundenserver.de
i:C = DE, O = Deutsche Telekom Security GmbH, CN = Telekom Security ServerID OV Class 2 CA
a

KEY: rsaEncryption, 3072 (bit); sigalg: RSA-SHA256
v:NotBefore: Apr 10 06:20:33 2025 GMT; NotAfter: Apr 14 23:59:59 2026 GMT
1 s:C = DE, O = Deutsche Telekom Security GmbH, CN = Telekom Security ServerID OV Class 2 CA
i:C = DE, O = T-Systems Enterprise Services GmbH, OU = T-Systems Trust Center, CN = T-TeleSec GlobalRoot Class 2
a

KEY: rsaEncryption, 3072 (bit); sigalg: RSA-SHA256
v:NotBefore: Aug 2 09:16:44 2022 GMT; NotAfter: Aug 2 23:59:59 2027 GMT
---
Server certificate
-----BEGIN CERTIFICATE-----
MIIJyzCCCDOgAwIBAgIQJ+/Vt7F2EOSuhtQN6pea1zANBgkqhkiG9w0BAQsFADBo
MQswCQYDVQQGEwJERTEnMCUGA1UECgweRGV1dHNjaGUgVGVsZWtvbSBTZWN1cml0
eSBHbWJIMTAwLgYDVQQDDCdUZWxla29tIFNlY3VyaXR5IFNlcnZlcklEIE9WIENs
YXNzIDIgQ0EwHhcNMjUwNDEwMDYyMDMzWhcNMjYwNDE0MjM1OTU5WjBrMQswCQYD
VQQGEwJERTEYMBYGA1UECBMPUmhlaW5sYW5kLVBmYWx6MRIwEAYDVQQHEwlNb250
YWJhdXIxETAPBgNVBAoTCElPTk9TIFNFMRswGQYDVQQDExJteC5rdW5kZW5zZXJ2
ZXIuZGUwggGiMA0GCSqGSIb3DQEBAQUAA4IBjwAwggGKAoIBgQC1HupYZ4y0eVu5
ASg9bYz/VM6K3SNSBqtVpjFyOw5epjU5O1q5NIF75UzamF7TKoEpwFIHU9z2X59O
47sya+FHdY+amLQPAOQh7AMQ84JaRS4xLg5D3/hPMmL0U9c/Gd7JsMsMV8+RW6hX
CCf4vVuYiErNlfsl2XWuVlnqsopLLGZY9QVyHlpeTwmlVVQn2auwNI7MMt9BlP8T
iM8MA8fqzt1BWQfroDtrUKkN5snhmrSO8zbjQEDSFkj1BkX4pY06KmzbrWV2SKaS
q5H/jbgL84A1qVRX8qyZL9wFUwP9fSGT/d7XGJdnrFaOov7cwOKOzeJ0Nn2sP4NI
IggMFm8VC3/qQ+5qePfGLYhHm0D/mNTyhYSct9o8A4iNsmJPYM/lN12EHxMfp3Gm
1J4YWLfyDyLg/2vGQ6dUxBtCYNLkAiBbcYbB0COTDbne3U+94ePHFoOCJ+hO2OYe
uD40N5vkHPQJOKvH0EYOT5MYnk4QDlU5O1dQvOuMU2e/qtYL2ycCAwEAAaOCBWww
ggVoMB8GA1UdIwQYMBaAFBwFk7F/qDQwjFLglkCgcqMQXeD/MA4GA1UdDwEB/wQE
AwIFoDAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYBBQUHAwEwHQYDVR0OBBYEFAHa
cm3+JjncStz2NF24ZIUS/GmNMFMGA1UdIARMMEowSAYGZ4EMAQICMD4wPAYIKwYB
BQUHAgEWMGh0dHA6Ly9kb2NzLnNlcnZlcmlkLnRlbGVzZWMuZGUvY3BzL3NlcnZl
cmlkLmh0bTBeBgNVHR8EVzBVMFOgUaBPhk1odHRwOi8vY3JsLnNlcnZlcmlkLnRl
bGVzZWMuZGUvcmwvVGVsZWtvbV9TZWN1cml0eV9TZXJ2ZXJJRF9PVl9DbGFzc18y
X0NBLmNybDCBnwYIKwYBBQUHAQEEgZIwgY8wMQYIKwYBBQUHMAGGJWh0dHA6Ly9v
Y3NwLnNlcnZlcmlkLnRlbGVzZWMuZGUvb2NzcHIwWgYIKwYBBQUHMAKGTmh0dHA6
Ly9jcnQuc2VydmVyaWQudGVsZXNlYy5kZS9jcnQvVGVsZWtvbV9TZWN1cml0eV9T
ZXJ2ZXJJRF9PVl9DbGFzc18yX0NBLmNydDAMBgNVHRMBAf8EAjAAMIIBHwYDVR0R
BIIBFjCCARKCEm14Lmt1bmRlbnNlcnZlci5kZYIUbXgwMC5rdW5kZW5zZXJ2ZXIu
ZGWCFG14MDEua3VuZGVuc2VydmVyLmRlghlteDAwLmVtaWcua3VuZGVuc2VydmVy
LmRlghlteDAxLmVtaWcua3VuZGVuc2VydmVyLmRlghBteDAwLmlvbm9zLmNvLnVr
gg1teDAwLmlvbm9zLmRlgg1teDAwLmlvbm9zLmVzgg1teDAwLmlvbm9zLmZygg1t
eDAwLmlvbm9zLml0ghBteDAxLmlvbm9zLmNvLnVrgg1teDAxLmlvbm9zLmRlgg1t
eDAxLmlvbm9zLmVzgg1teDAxLmlvbm9zLmZygg1teDAxLmlvbm9zLml0MIICbQYK
KwYBBAHWeQIEAgSCAl0EggJZAlcAdQAOV5S8866pPjMbLJkHs/eQ35vCPXEyJd0h
qSWsYcVOIQAAAZYeW4HFAAAEAwBGMEQCIBLymA1J/70UBWSsPfPhXuDn/iIASoPT
ueZoXRk5UojQAiAK8NEXRRzcVO4cvVqbEoxvMIucz4Demoo0IhKmuAFQdQB1AJaX
ZL9VWJet90OHaDcIQnfp8DrV9qTzNm5GpD8PyqnGAAABlh5bgVoAAAQDAEYwRAIg
MD1yhm+NKcS63RnOz+wyTLsIG6u0rvJIl3jGrgXyN34CIGau5ApSaet/jn77C6Lc
FV2BCUHVVCJaaktEWPUQWxLPAHcAGYbUxyiqb/66A294Kk0BkarOLXIxD67OXXBB
LSVMx9QAAAGWHluDYwAABAMASDBGAiEA9rAJvCjzYk23FUf0+VtTI6IpYrT9uRZM
NDvaLzAuSWUCIQCvqV0dxkM+DWVj5NVTy3Zp+fFT4LJ1p4n0mLdWTrGxkQB2AEmc
m2neHXzs/DbezYdkprhbrwqHgBnRVVL76esp3fjDAAABlh5bgW4AAAQDAEcwRQIh
AMaoYcuKotRbQL8R4LvPJZUyqW4BIrF26rimIRsnVciUAiBgJBf7yfZ/IA6yWyt3
BdyVaL9KsNbSJ2B2ApWBNXHM7gB2AGQRxGykEuyniRyiAi4AvKtPKAfUHjUnq+r+
1QPJfc3wAAABlh5bgg4AAAQDAEcwRQIhAIH7CD4stu90ZH3TYKDB/Ue6+aOp29T+
jwOiNh8ztlu0AiARN2Id6gq8tPqcOPa2+OclKaYdxtC4L48nYTugbyhKNTANBgkq
hkiG9w0BAQsFAAOCAYEAKUrbKE1yoO5OoS029PPZLvKBdhT46gXLO8hd5Id0wpSb
3U4IR99E+r1ocVxvpIczjLRzaQx4K0K1vzHQK5HBlmaC7e2NhBHacYl1hO9SnBBh
JtvjOgha8cAt+Q5B7Y1VCz/xkXaUyPUl6BpAxTQa7NWTv8LBDaica3t4a0bBRMAX
NLirc7dOv/l+8h+uNUuHJYGoRWuGSkDH8qV6I0AOSoNlY9Y0Dkw7JEuif/zT5+L2
ZpuAq4ha3Q7BPlmUSXj335Sxl2lgqc8O9zQuZhpNVs+OHRPw0pLGLOGM6mDDmEKM
yFnom/au0Il9dI950sWgx4KoajtxSt2p7MWxa2XtQ+HN1xPwg4J1LHqzUi+0Pwk0
q7kvwrDYYPQQCLZAAXbdaIu62jGwqvk/nUNdyGKQzpiLSA10tuARzZJS/Y0xLpYb
SDFlK5wCD9y/4aDWyRi33Y/hBPm7Os2PTZweRtbNUn10XipNcZ2tgJtDOt8J4YUH
Gpz0PL4AdC+HeB6WXN2h
-----END CERTIFICATE-----
subject=C = DE, ST = Rheinland-Pfalz, L = Montabaur, O = IONOS SE, CN =
mx.kundenserver.de
issuer=C = DE, O = Deutsche Telekom Security GmbH, CN = Telekom Security ServerID OV Class 2 CA
---
No client certificate CA names sent
Peer signing digest: SHA256
Peer signature type: RSA-PSS
Server Temp Key: ECDH, prime256v1, 256 bits
---
SSL handshake has read 4905 bytes and written 784 bytes
Verification: OK
---
New, TLSv1.3, Cipher is TLS_AES_256_GCM_SHA384
Server public key is 3072 bit
Secure Renegotiation IS NOT supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
Early data was not sent
Verify return code: 0 (ok)
---
250 STARTTLS
421
kundenserver.de Service closing transmission channel - command timeout
closed
Kind regards