Hello Guys,
currently running proxmox 7.2-3 on a dedicated server. I got only one public ip (eno1) and two bridges (vmbr0, vmbr1). The idea is to have some VM's over vmbr0 (more management like tooling) and some others over vmbr1. Does that even make sense to set it up that way?
I tried to setup the port forwarding, but I can't reach the services on the VM. The VM is a rocky linux (selinux enabled). Datecenter firewall is On and has the entries
The Mailserver VM is using
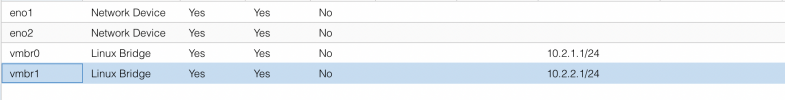
My /etc/network/interfaces file looks like:
The mailserver setup, DNS settings etc. seems to be okay. I can receive emails, I can send emails via webmail. I just can't setup my local email client (Apple Mail), it shows: "Unable to verify account name or password".
I'm pretty sure this setup here between eno1, eno2, vmbr0, vmbr1 and the fact that I got only one public IP is simply wrong. So I would need a little help here.
Thanks a lot.
currently running proxmox 7.2-3 on a dedicated server. I got only one public ip (eno1) and two bridges (vmbr0, vmbr1). The idea is to have some VM's over vmbr0 (more management like tooling) and some others over vmbr1. Does that even make sense to set it up that way?
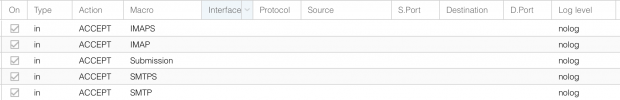
I tried to setup the port forwarding, but I can't reach the services on the VM. The VM is a rocky linux (selinux enabled). Datecenter firewall is On and has the entries
IN ACCEPT IMAP, IN ACCEPT IMAPS, ... etc. . Firewall on the Node is on as well, no further rules specified.The Mailserver VM is using
vmbr1. At the beginning I had the SMTP, IMAP port forwardings only on vmbr1, then added them to vmbr0 as well.My /etc/network/interfaces file looks like:
Bash:
auto eno1
iface eno1 inet dhcp
auto eno2
iface eno2 inet manual
auto vmbr0
iface vmbr0 inet static
address 10.2.1.1/24
bridge-ports none
bridge-stp off
bridge-fd 0
post-up echo 1 > /proc/sys/net/ipv4/ip_forward
post-up iptables -t nat -A POSTROUTING -s '10.2.1.0/24' -o eno1 -j MASQUERADE
post-down iptables -t nat -D POSTROUTING -s '10.2.1.0/24' -o eno1 -j MASQUERADE
post-up iptables -t raw -I PREROUTING -i fwbr+ -j CT --zone 1
post-down iptables -t raw -D PREROUTING -i fwbr+ -j CT --zone 1
#post-up iptables -t raw -I POSTROUTING -i fwbr+ -j CT --zone 1
#post-down iptables -t raw -D POSTROUTING -i fwbr+ -j CT --zone 1
# port forwarding
post-up iptables -t nat -A PREROUTING -i eno1 -p udp --dport 51820 -j DNAT --to 10.2.1.2:51820
post-down iptables -t nat -D PREROUTING -i eno1 -p udp --dport 51820 -j DNAT --to 10.2.1.2:51820
post-up iptables -t nat -A PREROUTING -i eno1 -p tcp --dport 2222 -j DNAT --to 10.2.1.2:22
post-down iptables -t nat -D PREROUTING -i eno1 -p tcp --dport 2222 -j DNAT --to 10.2.1.2:22
# SMTP
post-up iptables -t nat -A PREROUTING -i eno1 -p tcp --dport 25 -j DNAT --to 10.2.2.2:25
post-down iptables -t nat -D PREROUTING -i eno1 -p tcp --dport 25 -j DNAT --to 10.2.2.2:25
# SMTPS
...
# Submission
...
# IMAP
...
# IMAPS
...
auto vmbr1
iface vmbr1 inet static
address 10.2.2.1/24
bridge-ports none
bridge-stp off
bridge-fd 0
post-up echo 1 > /proc/sys/net/ipv4/ip_forward
post-up iptables -t nat -A POSTROUTING -s '10.2.2.0/24' -o eno1 -j MASQUERADE
post-down iptables -t nat -D POSTROUTING -s '10.2.2.0/24' -o eno1 -j MASQUERADE
# port forwarding
# SMTP
post-up iptables -t nat -A PREROUTING -i eno1 -p tcp --dport 25 -j DNAT --to 10.2.2.2:25
post-down iptables -t nat -D PREROUTING -i eno1 -p tcp --dport 25 -j DNAT --to 10.2.2.2:25
# SMTPS
...
# Submission
...
# IMAP
...
# IMAPS
...The mailserver setup, DNS settings etc. seems to be okay. I can receive emails, I can send emails via webmail. I just can't setup my local email client (Apple Mail), it shows: "Unable to verify account name or password".

I'm pretty sure this setup here between eno1, eno2, vmbr0, vmbr1 and the fact that I got only one public IP is simply wrong. So I would need a little help here.
Thanks a lot.
Last edited: