1) Is pfSense on your Proxmox server or elsewhere?
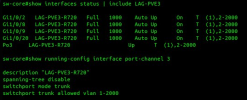
2) You're certain the link to the switch is 100% fine? If not, I would temporarily simplify by backing off from LACP/LAG group. Keep it a simple one-connection link until you have this solved. Fewer variables.
3) Here's how I have trunk + VLAN-for-VM set up:
First, my LACP bond. NOTE: I have never succeeded in attaining VLAN smarts on the bond itself.
Mine connects to a Netgear (not-so) "smart switch", which only supports layer2. I tried to look up the hash policies for yours. It's quite complex; not sure which policy would be correct in either direction!
Make sure you use a policy that linux can understand!
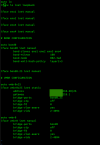
auto bond0
iface bond0 inet manual
bond-slaves ens4f1 ens4f2
bond-miimon 100
bond-mode 802.3ad
bond-xmit-hash-policy layer2
#LAN LAG
Then in the host, a trunk for pfSense to my switch. Not sure it matters but in my case pfSense is in a host VM.
NOTE that I had to define bridge-pvid for everything to work correctly. That identifies the VLAN that will be untagged..
auto vmbr2
iface vmbr2 inet manual
bridge-ports bond0
bridge-stp off
bridge-fd 0
bridge-vlan-aware yes
bridge-vids 2-4094
bridge-pvid 71
#LACP LAG 4 LAN
Then in a specific VM configuration (
/etc/pve/nodes/<node>/qemu-server/<nnn>.conf):
net1: virtio=<mac>,bridge=vmbr2,tag=9
I can grab as many virtual NICs as I want off of vmbr2. I have a pfSense VM that gets the "raw" vmbr2. I have a complex VM with four virtual NICs each talking to a different VLAN. pfSense supplies DHCP to every VLAN, and every VM correctly obtains IP's via DHCP on any VLAN.
I also created a static virtual nic in the host tapping into a specific VLAN. In this case while I could have used DHCP I didn't because I want the core infrastructure to function even when pfSense/DHCP is down:
auto vmbr2.77
iface vmbr2.77 inet static
address 192.168.7.236/24
#host diagnostic port on .7
4) If you need to debug LACP, this person did some intense debugging. When you get there this might be informative...
https://tchien.com/technical-ramblings/2021/4/8/proxmox-and-unifi-lacp-vlans-and-bridges
I'm away for a bit now. I hope this is helpful!