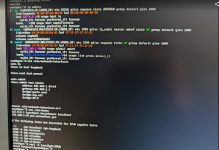
22:18:15.874019 eno1 In IP 192.168.1.20.51066 > 192.168.1.151.22: Flags [P.], seq 4170255141:4170256573, ack 997982235, win 255, length 1432
22:18:15.874025 vmbr0 In IP 192.168.1.20.51066 > 192.168.1.151.22: Flags [P.], seq 0:1432, ack 1, win 255, length 1432
22:18:15.874047 vmbr0 Out IP 192.168.1.151.22 > 192.168.1.20.51066: Flags [R], seq 997982235, win 0, length 0
22:18:15.874051 eno1 Out IP 192.168.1.151.22 > 192.168.1.20.51066: Flags [R], seq 997982235, win 0, length 0
22:18:21.020029 vmbr0 Out ARP, Request who-has 192.168.1.20 tell 192.168.1.151, length 28
22:18:21.020037 eno1 Out ARP, Request who-has 192.168.1.20 tell 192.168.1.151, length 28
22:18:21.076889 eno1 In ARP, Reply 192.168.1.20 is-at b8:1e:a4:f0:fd:49, length 46
22:18:21.076894 vmbr0 In ARP, Reply 192.168.1.20 is-at b8:1e:a4:f0:fd:49, length 46
22:18:22.037784 eno1 In ARP, Request who-has 192.168.1.151 (c4:34:6b:64:da:61) tell 192.168.1.20, length 46
22:18:22.037790 vmbr0 In ARP, Request who-has 192.168.1.151 (c4:34:6b:64:da:61) tell 192.168.1.20, length 46
22:18:22.037798 vmbr0 Out ARP, Reply 192.168.1.151 is-at c4:34:6b:64:da:61, length 28
22:18:22.037801 eno1 Out ARP, Reply 192.168.1.151 is-at c4:34:6b:64:da:61, length 28
22:18:55.206706 eno1 In IP 192.168.1.20.52902 > 192.168.1.151.8006: Flags [.], ack 2035807393, win 255, length 0
22:18:55.206712 vmbr0 In IP 192.168.1.20.52902 > 192.168.1.151.8006: Flags [.], ack 1, win 255, length 0
22:18:55.206734 vmbr0 Out IP 192.168.1.151.8006 > 192.168.1.20.52902: Flags [R], seq 2035807393, win 0, length 0
22:18:55.206738 eno1 Out IP 192.168.1.151.8006 > 192.168.1.20.52902: Flags [R], seq 2035807393, win 0, length 0
22:18:55.206743 eno1 In IP 192.168.1.20.62407 > 192.168.1.151.8006: Flags [.], ack 207313155, win 255, length 0
22:18:55.206743 vmbr0 In IP 192.168.1.20.62407 > 192.168.1.151.8006: Flags [.], ack 1, win 255, length 0
22:18:55.206746 vmbr0 Out IP 192.168.1.151.8006 > 192.168.1.20.62407: Flags [R], seq 207313155, win 0, length 0
22:18:55.206747 eno1 Out IP 192.168.1.151.8006 > 192.168.1.20.62407: Flags [R], seq 207313155, win 0, length 0
22:19:00.444022 vmbr0 Out ARP, Request who-has 192.168.1.20 tell 192.168.1.151, length 28
22:19:00.444030 eno1 Out ARP, Request who-has 192.168.1.20 tell 192.168.1.151, length 28
22:19:00.498828 eno1 In ARP, Reply 192.168.1.20 is-at b8:1e:a4:f0:fd:49, length 46
22:19:00.498834 vmbr0 In ARP, Reply 192.168.1.20 is-at b8:1e:a4:f0:fd:49, length 46
22:19:26.313873 eno1 In IP 192.168.1.20.57841 > 192.168.1.151.8006: Flags [.], ack 3069751237, win 255, length 0
22:19:26.313878 vmbr0 In IP 192.168.1.20.57841 > 192.168.1.151.8006: Flags [.], ack 1, win 255, length 0
22:19:26.313899 vmbr0 Out IP 192.168.1.151.8006 > 192.168.1.20.57841: Flags [R], seq 3069751237, win 0, length 0
22:19:26.313903 eno1 Out IP 192.168.1.151.8006 > 192.168.1.20.57841: Flags [R], seq 3069751237, win 0, length 0
22:19:26.313964 eno1 In IP 192.168.1.20.58077 > 192.168.1.151.8006: Flags [.], ack 389731784, win 255, length 0
22:19:26.313966 vmbr0 In IP 192.168.1.20.58077 > 192.168.1.151.8006: Flags [.], ack 1, win 255, length 0
22:19:26.313970 vmbr0 Out IP 192.168.1.151.8006 > 192.168.1.20.58077: Flags [R], seq 389731784, win 0, length 0
22:19:26.313972 eno1 Out IP 192.168.1.151.8006 > 192.168.1.20.58077: Flags [R], seq 389731784, win 0, length 0
22:19:31.676021 vmbr0 Out ARP, Request who-has 192.168.1.20 tell 192.168.1.151, length 28
22:19:31.676029 eno1 Out ARP, Request who-has 192.168.1.20 tell 192.168.1.151, length 28
22:19:31.683320 eno1 In ARP, Reply 192.168.1.20 is-at b8:1e:a4:f0:fd:49, length 46
22:19:31.683326 vmbr0 In ARP, Reply 192.168.1.20 is-at b8:1e:a4:f0:fd:49, length 46