Hey,
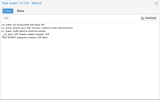
Where does the VLAN tagging of the Ethernet frames take place?
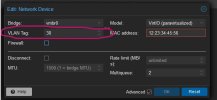
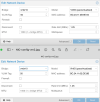
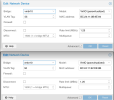
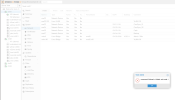
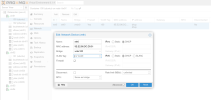
When I set the VLAN tag on the VM, the VLAN tagging is performed on the VM's network interface. So outgoing packets from the VM receive the VLAN tag.
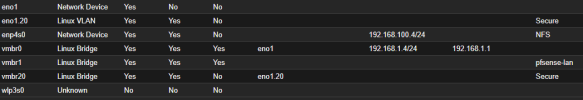
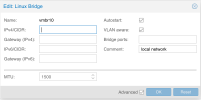
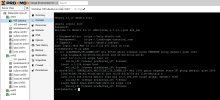
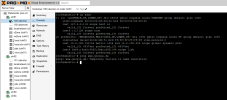
But what if I use “Linux VLAN”? Or just use SDN? At what level is VLAN tagging then performed?
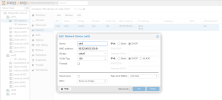
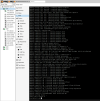
If I do a mixed operation, i.e. tag VM-01 in the config with ID=100 and set VM-02 to the "Linux VLAN" ID=100, both VMs have no network.
Does tagging get in the way?
Where does the VLAN tagging of the Ethernet frames take place?
When I set the VLAN tag on the VM, the VLAN tagging is performed on the VM's network interface. So outgoing packets from the VM receive the VLAN tag.
But what if I use “Linux VLAN”? Or just use SDN? At what level is VLAN tagging then performed?
If I do a mixed operation, i.e. tag VM-01 in the config with ID=100 and set VM-02 to the "Linux VLAN" ID=100, both VMs have no network.
Does tagging get in the way?