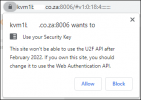
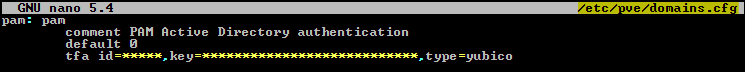
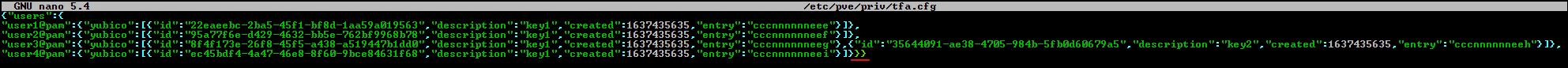
I recognized that PVE 7.1 supports WebAuthn so I decided to migrate from U2F to it.
But unfortunately it fails with following error message:
`The user verified even through discouragement`
But unfortunately it fails with following error message:
`The user verified even through discouragement`