Hello,
I am very new to this.
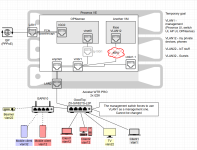
I aim to establish the following configuration (VLANs can be updated as I gain more knowledge). It's nothing super ambitious - I'd like to have decent backup NAS and an owncloud drive. Plus some security/traffic and flexibility.
I have Aoostar WTR Pro.
LAN1 - PCIe passthrough to OPNsense - OK.
LAN2 - for my home network.
OPNsense acts as a firewall and router (and VLAN router), unbound DNS in the future for an owncloud.
There is a limitation with my switch: VLAN 1 is set to be management and cannot be changed.
I have not considered a dedicated 'router' machine; I hope this is achievable with this single mini PC.
A diagram of what I aim to do:
Using LLMs as a guide, I had the following setup.
Interfaces on Proxmox:
An LLM told me that OPNsense manages VLANs, so that works. Then, led by LLM, I set a trunk port on my switch in the following way:
The VLAN4000 acts as a sacrifice VLAN.
And, one of the other ports serves as an access port for VLAN 1.
Surprisingly, this works - I can see 802.1Q packets while pinging devices. All is fine.
And here is the first puzzle. If VLAN 1 is untagged, where does all the 802.1Q traffic come from? I can imagine that the switch releases tagged packets, but Proxmox, when pinging OPNsense, also sends tagged frames.
The "ip a" shows nothing suspicious.
So, I prepared another VM - just a small Debian system for the console for testing (I set VLAN1 for testing purposes). Right after I started this machine, it went into eternal hunting grounds.
Proxmox UI displays 'Guest not running' on client1-vlan1.
The Proxmox console still allows me to ping OPNsense, but the switch (so local LAN) can no longer access anything. Proxmox cannot reach out the laptop in VLAN1
The "ip a" shows now a number of new entities:
And tcpdump on tap101i0 shows 'ethertype ARP' - so no VLANs....
So I am trying a different approach, brand new interfaces:
Here - I can ping Proxmox from VLAN1 laptopt and vice versa but not the OPNsense itsel.
Then, having executed command
- I can ping OPNsense IPs.
So, I start VM101, and I can see it starts in ProxmoUI. Nothing breaks. All pings work.
Still untagged VLAN1 - but tcpdump lists '802.1Q'. Do not get this at all.
The "ip a" shows now a number of new entities:
In the case you have read up to this moment, I'd appreciate a recommendation on how to improve it.
I've read that
can be included in the Proxmox startup procedure, but at the moment, I don't like it - it doesn't seem clean. Not to mention that the interfaces of the new VM still show 'Untagged,' which is unusual. For example, if I set VLAN1 on the switch to default on a trunk port, it strips the 'vlan' marker from packets.
I can see two options - but I feel I am hitting the wall:
Pawel
I am very new to this.
I aim to establish the following configuration (VLANs can be updated as I gain more knowledge). It's nothing super ambitious - I'd like to have decent backup NAS and an owncloud drive. Plus some security/traffic and flexibility.
I have Aoostar WTR Pro.
LAN1 - PCIe passthrough to OPNsense - OK.
LAN2 - for my home network.
OPNsense acts as a firewall and router (and VLAN router), unbound DNS in the future for an owncloud.
There is a limitation with my switch: VLAN 1 is set to be management and cannot be changed.
I have not considered a dedicated 'router' machine; I hope this is achievable with this single mini PC.
A diagram of what I aim to do:

Using LLMs as a guide, I had the following setup.
Interfaces on Proxmox:
Code:
...
iface eno1 inet manual #LAN1
iface enp3s0 inet manual #LAN2
auto vmbr1
iface vmbr1 inet manual
bridge-ports enp3s0
bridge-stp off
bridge-fd 0
auto vmbr1.1
iface vmbr1.1 inet static
address 192.168.1.4/24
gateway 192.168.1.1An LLM told me that OPNsense manages VLANs, so that works. Then, led by LLM, I set a trunk port on my switch in the following way:
Code:
interface xe1/10
switchmode port trunk
switchport trunk native vlan 4000
switchport trunk allowed vlan add 1
switchport trunk allowed vlan add 12
switchport trunk allowed vlan add 22
switchport trunk allowed vlan add 32The VLAN4000 acts as a sacrifice VLAN.
And, one of the other ports serves as an access port for VLAN 1.
Surprisingly, this works - I can see 802.1Q packets while pinging devices. All is fine.
Code:
# bridge vlan show
port vlan-id
enp3s0 1 PVID Egress Untagged
vmbr1 1 PVID Egress Untagged
tap100i1 1 PVID Egress UntaggedThe "ip a" shows nothing suspicious.
So, I prepared another VM - just a small Debian system for the console for testing (I set VLAN1 for testing purposes). Right after I started this machine, it went into eternal hunting grounds.
Proxmox UI displays 'Guest not running' on client1-vlan1.
The Proxmox console still allows me to ping OPNsense, but the switch (so local LAN) can no longer access anything. Proxmox cannot reach out the laptop in VLAN1
The "ip a" shows now a number of new entities:
- tap101i0 (a new vm interface I suppose)
- vmbr1v1 ( what's this?) - link/ether - to LAN2
- enp3s0.1@enp3s0 (huh - vlan1 device I think) - link/ether - to LAN2
- fwbr101i0 (?)
- fwpr101p0@fwln101i0 (?)
- fwln101i0@fwpr101p0 (?)
Code:
# bridge vlan show
port vlan-id
enp3s0 1 PVID Egress Untagged
vmbr1 1 PVID Egress Untagged
tap100i1 1 PVID Egress Untagged
tap101i0 1 PVID Egress Untagged
vmbrv1 1 PVID Egress Untagged
enp3s0.1 1 PVID Egress Untagged
fwbr101i0 1 PVID Egress Untagged
fwpr101i0 1 PVID Egress Untagged
fwln101i0 1 PVID Egress UntaggedAnd tcpdump on tap101i0 shows 'ethertype ARP' - so no VLANs....
So I am trying a different approach, brand new interfaces:
Code:
...
iface eno1 inet manual #LAN1
iface enp3s0 inet manual #LAN2
auto vmbr1
iface vmbr1 inet manual
bridge-ports enp3s0
bridge-stp off
bridge-fd 0
bridge-vlan-aware yes
bridge-vids 1,12,22,32
bridge-pvid 4000
auto vmbr1.1
iface vmbr1.1 inet static
address 192.168.1.4/24
gateway 192.168.1.1Here - I can ping Proxmox from VLAN1 laptopt and vice versa but not the OPNsense itsel.
Code:
# bridge vlan show
port vlan-id
enp3s0 1
12
22
32
4000 PVID Egress Untagged
vmbr1 1
tap100i1 1 PVID Egress Untagged
2
3
... all vlan tags hereThen, having executed command
Code:
bridge vlan add vid 1 dev tap100i1So, I start VM101, and I can see it starts in ProxmoUI. Nothing breaks. All pings work.
Code:
# bridge vlan show
port vlan-id
enp3s0 1
12
22
32
4000 PVID Egress Untagged
vmbr1 1
tap100i1 1 PVID Egress Untagged
2
3
... all vlan tags here
tap101i0 1 PVID Egress Untagged
fwbr101i0 1 PVID Egress Untagged
fwpr101i0 1 PVID Egress Untagged
fwln101i0 1 PVID Egress Untagged
Code:
The "ip a" shows now a number of new entities:
- tap101i0 (a new vm interface I suppose)
- fwbr101i0 (?)
- fwpr101p0@fwln101i0 (?)
- fwln101i0@fwpr101p0 (?)
In the case you have read up to this moment, I'd appreciate a recommendation on how to improve it.
I've read that
Code:
bridge vlan add vid one dev tap100i1I can see two options - but I feel I am hitting the wall:
- Manual setup of VLANs in Proxmox (so enp3s0.1 and vmbr1.1)
- Reconfigure VLAN1 to be untagged
- Any other recommendations?
- How to configure tap100i1 (from OPNsense or Proxmox) so that it respects the default VLAN as the 4000 one.
Pawel
Last edited:

