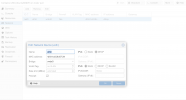
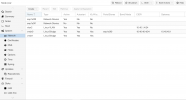
I have a VLAN (VLAN2) that I recently setup to separate all my hosts that are accessible from outside my network from the internal hosts. Everything was working fine until I made two changes (not sure which one broke the VLAN). The first change was upgrading my PVE-7.0-2 (or something close to that version) to PVE-7.2-5. The second change was removing all my DHCP leases but then realizing that my switch had a DHCP IP and that was now gone. I noticed this when I noticed I couldn't access any of my machines on VLAN 2. I couldn't get the switch to take an IP so I reset the switch to factory default. Since these two changes I haven't been able to get any traffic to flow on VLAN 2. I have tried assigning static IPs and also tried DHCP and there seems to be no connection between my VMs and the firewall. The switch config was pretty simple before and the only setting I question is whether 802.1Q should be enabled or disabled or does it matter at all? (see screenshot 1). 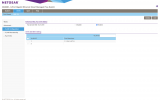
I haven't changed any of the settings on the firewall and I can ping both the firewall and my PVE server on VLAN 2 so I know the network is working and I assume the switch isn't causing issues because I can connect with my server on VLAN 2 but none of my VLAN 2 machines are getting an IP address and even with static IPs they can't reach anything, and can't be reached on any network when all was working fine before. My firewall is a pfsense firewall and the switch is a Netgear GS308E. I will include some screenshots of my configs. Any help is greatly appreciated. Thanks in advance.

I haven't changed any of the settings on the firewall and I can ping both the firewall and my PVE server on VLAN 2 so I know the network is working and I assume the switch isn't causing issues because I can connect with my server on VLAN 2 but none of my VLAN 2 machines are getting an IP address and even with static IPs they can't reach anything, and can't be reached on any network when all was working fine before. My firewall is a pfsense firewall and the switch is a Netgear GS308E. I will include some screenshots of my configs. Any help is greatly appreciated. Thanks in advance.
Attachments
Last edited: