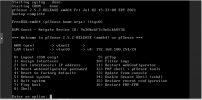
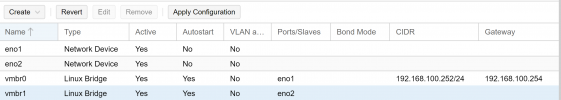
Your mainboard doesn't got onboard NICs? Wasn't able to see another NIC beside the dual 10Gbit one.
So your NIC is "03:00" with the functions "03:00.0" and "03:00.1":
And the NIC got it's own group "31" which no other device is using...
...but both functions are in the same group. So you should be able to pass the NIC to a pfsense VM but I think only both functions together. So you would need to pass both ports to the VM at the same time.
If you don'T got another onboard NIC that could be problematic, because as soon as you passthrough the complete NIC with both ports to the VM your host woulnd't have any NIC left, so you wouldn't be able to use the PVE webUI/SSH anymore and your host would be offline.
And yes, if you blacklist the driver of your only NIC PVE can't use it anymore, so you locked yourself out of the host. You could attach a display/keyboard or use a BMS to undo the driver blacklisting to get access again.
So your NIC is "03:00" with the functions "03:00.0" and "03:00.1":
Code:
03:00.0 Ethernet controller: Broadcom Limited NetXtreme II BCM57810 10 Gigabit Ethernet (rev 10)
03:00.1 Ethernet controller: Broadcom Limited NetXtreme II BCM57810 10 Gigabit Ethernet (rev 10)And the NIC got it's own group "31" which no other device is using...
Code:
/sys/kernel/iommu_groups/31/devices/0000:03:00.0
/sys/kernel/iommu_groups/31/devices/0000:03:00.1If you don'T got another onboard NIC that could be problematic, because as soon as you passthrough the complete NIC with both ports to the VM your host woulnd't have any NIC left, so you wouldn't be able to use the PVE webUI/SSH anymore and your host would be offline.
And yes, if you blacklist the driver of your only NIC PVE can't use it anymore, so you locked yourself out of the host. You could attach a display/keyboard or use a BMS to undo the driver blacklisting to get access again.
Last edited: