Unified cgroup v2 layout Upgrade warning PVE 6.4 to 7.0
- Thread starter yswery
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
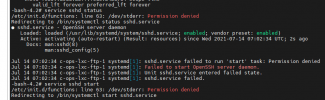
Well this is almost a solution, minus the fact that nothing runs, you get permissioned denied. Oi. I think my only hope is to move it to a host I have not upgraded yet. Can't reset root password, can't change passwords. I entered this CT via pct enter <ctid>
Attachments
Remove the unprivileged var conf and instead try adding to yur LXC conf the followingWell this is almost a solution, minus the fact that nothing runs, you get permissioned denied. Oi. I think my only hope is to move it to a host I have not upgraded yet. Can't reset root password, can't change passwords. I entered this CT via pct enter <ctid>
Code:
lxc.cgroup.devices.allow =
lxc.cgroup.devices.deny =Let us know how that goes?
There isnt a newer version of systemd in ubuntu 16.04.
Even with ESM, i have that on one machine.
Even with ESM, i have that on one machine.
What about backporting the systemd version? Anyone tried that?There isnt a newer version of systemd in ubuntu 16.04.
Even with ESM, i have that on one machine.
That worked for me. Thanks for your help.Remove the unprivileged var conf and instead try adding to yur LXC conf the following
Code:lxc.cgroup.devices.allow = lxc.cgroup.devices.deny =
Let us know how that goes?
I had to set it for all containers and not only for the old 16.04 one. Time to get rid of the Ubuntu 16.04 Container and remove all the settings again...
Remove the unprivileged var conf and instead try adding to yur LXC conf the following
Code:lxc.cgroup.devices.allow = lxc.cgroup.devices.deny =
Let us know how that goes?
A patch for privileged containers running on legacy cgroup layouts was sent to the pve-devel list for discussion:
https://lists.proxmox.com/pipermail/pve-devel/2021-July/049452.html
I'd suggest to remove those lines again, once a working version becomes available, because this essentially allows a privileged container (=root on host) to access arbitrary devices - you lose quite a bit of the isolation of the container.
A patch for privileged containers running on legacy cgroup layouts was sent to the pve-devel list for discussion:
https://lists.proxmox.com/pipermail/pve-devel/2021-July/049452.html
it's already available on the `pvetest` repository:
https://pve.proxmox.com/pve-docs/chapter-sysadmin.html#sysadmin_test_repo
lxc-pve version 4.0.9-3
Update systemd in the centos 7 container
https://maciej.lasyk.info/2016/Dec/16/systemd-231-latest-in-centos-7-thx-to-facebook/
Bash:
wget https://copr.fedorainfracloud.org/coprs/jsynacek/systemd-backports-for-centos-7/repo/epel-7/jsynacek-systemd-backports-for-centos-7-epel-7.repo -O /etc/yum.repos.d/jsynacek-systemd-centos-7.repo
yum update systemdhttps://maciej.lasyk.info/2016/Dec/16/systemd-231-latest-in-centos-7-thx-to-facebook/
have simmiler issue:Update systemd in the centos 7 container
Bash:wget https://copr.fedorainfracloud.org/coprs/jsynacek/systemd-backports-for-centos-7/repo/epel-7/jsynacek-systemd-backports-for-centos-7-epel-7.repo -O /etc/yum.repos.d/jsynacek-systemd-centos-7.repo yum update systemd
https://maciej.lasyk.info/2016/Dec/16/systemd-231-latest-in-centos-7-thx-to-facebook/
i tried to do it, but the centos lxc dont have access internet
I've just updated systemd in one of my CentOS-7 containers (as described above) to systemd-234 but when I reboot the container and re-run pve6to7 --full ...(sadly) it still reports the same problem:
"WARN: Found at least one CT (xxx) which does not support running in a unified cgroup v2 layout. Either upgrade the Container distro or set systemd.unified_cgroup_hierarchy=0 in the Proxmox VE hosts' kernel cmdline! Skipping further CT compat checks"
Do you think this diagnostic might just be a "false positive"? Any further ideas would be very welcome... thanks people!
"WARN: Found at least one CT (xxx) which does not support running in a unified cgroup v2 layout. Either upgrade the Container distro or set systemd.unified_cgroup_hierarchy=0 in the Proxmox VE hosts' kernel cmdline! Skipping further CT compat checks"
Do you think this diagnostic might just be a "false positive"? Any further ideas would be very welcome... thanks people!
ooops, my bad - I just haven't properly woken up this morning ;-)
I've only just noticed that the WARNing (above) is now referring to a different container, so it looks like upgrading systemd did in fact fix the problem in the original container and I just have to roll out this update to the other CentOS-7 containers. Apologies for the noise!
I've only just noticed that the WARNing (above) is now referring to a different container, so it looks like upgrading systemd did in fact fix the problem in the original container and I just have to roll out this update to the other CentOS-7 containers. Apologies for the noise!
I have same problem whit centos7 ct on proxmox 5.4-3 moving to 7.1-7, after updateing systemd it works on new proxmox, thanks!!!
have simmiler issue:
i tried to do it, but the centos lxc dont have access internet
You can bring the network interface up with dhclient or by setting a static ip, or you can copy the rpm's to your host and then transfer them over to the container.
For example:
Bash:
$ pct enter YOURCONTAINERID
$ dhclient
$ wget https://copr.fedorainfracloud.org/coprs/jsynacek/systemd-backports-for-centos-7/repo/epel-7/jsynacek-systemd-backports-for-centos-7-epel-7.repo -O /etc/yum.repos.d/jsynacek-systemd-centos-7.repo
$ yum update systemdor
Bash:
# On your pve host
$ mkdir /root/systemd-backports && cd /root/systemd-backports
$ wget -r https://download.copr.fedorainfracloud.org/results/jsynacek/systemd-backports-for-centos-7/epel-7-x86_64/00580867-systemd/ --no-parent
$ cd download.copr.fedorainfracloud.org/results/jsynacek/systemd-backports-for-centos-7/epel-7-x86_64/00580867-systemd
$ for x in *.rpm; do pct push YOURCONTAINERID $x /root/$x; done
$ pct enter YOURCONTAINERID
$ yum localinstall *.rpmAlready answered here https://forum.proxmox.com/threads/proxmox-ve-8-0-released.129320/post-584579I have the same problem with Fedora35 and Fedora38 CT for which this should be ok, no ?
so pve7to8 gives warning
and here https://forum.proxmox.com/threads/pve7to8-cgroup-warning-incorrect.128721/post-584609