Hi.
Some of my customers are forwarding emails from their old addresses (ex.: @gmail.com to their new domain addresses). My PMG's are blocking some incoming mail that are forward from an ISP (Videotron). I need to be able to tell PMG to never check RBL and SPF rules for emails coming from all of Videotron servers, they had some I found so far:
alt12.smtp-out.videotron.ca, alt22.smtp-out.videotron.ca, alt32.smtp-out.videotron.ca and alt42.smtp-out.videotron.ca.
I'm afraid that I'll miss some more, so I thought about using a REGULAR EXPRESSION to add *.smtp-out.videotron.ca, but it's not working.
Then I tried adding only the IP adresses that I know, but even this is still blocked !
Here is some details for 3 emails from the TRACKING CENTER of PMG:
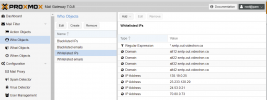
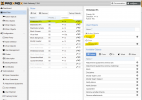
and now here is my setup:
What am I missing?
Thank you.
Some of my customers are forwarding emails from their old addresses (ex.: @gmail.com to their new domain addresses). My PMG's are blocking some incoming mail that are forward from an ISP (Videotron). I need to be able to tell PMG to never check RBL and SPF rules for emails coming from all of Videotron servers, they had some I found so far:
alt12.smtp-out.videotron.ca, alt22.smtp-out.videotron.ca, alt32.smtp-out.videotron.ca and alt42.smtp-out.videotron.ca.
I'm afraid that I'll miss some more, so I thought about using a REGULAR EXPRESSION to add *.smtp-out.videotron.ca, but it's not working.
Then I tried adding only the IP adresses that I know, but even this is still blocked !
Here is some details for 3 emails from the TRACKING CENTER of PMG:
Code:
Nov 15 10:46:56 pmg10 postfix/smtpd[2389421]: connect from alt22.smtp-out.videotron.ca[70.80.0.73]
Nov 15 10:46:57 pmg10 postfix/smtpd[2389421]: NOQUEUE: reject: RCPT from alt22.smtp-out.videotron.ca[70.80.0.73]: 554 5.7.1 <nancygroulx@aubutgroulx.ca>: Recipient address rejected: Rejected by SPF: 70.80.0.73 is not a designated mailserver for d.aubry%40cglmicro.ca (context mfrom, on pmg10.legardeur.net); from=<d.aubry@cglmicro.ca> to=<nancygroulx@aubutgroulx.ca> proto=ESMTP helo=<alt22.smtp-out.videotron.ca>
Nov 15 10:47:57 pmg10 postfix/smtpd[2389421]: disconnect from alt22.smtp-out.videotron.ca[70.80.0.73] ehlo=2 starttls=1 mail=1 rcpt=0/1 rset=1 quit=1 commands=6/7
Nov 15 10:52:02 pmg10 postfix/smtpd[2405904]: connect from alt32.smtp-out.videotron.ca[24.53.0.21]
Nov 15 10:52:03 pmg10 postfix/smtpd[2405904]: NOQUEUE: reject: RCPT from alt32.smtp-out.videotron.ca[24.53.0.21]: 554 5.7.1 <nancygroulx@aubutgroulx.ca>: Recipient address rejected: Rejected by SPF: 24.53.0.21 is not a designated mailserver for d.aubry%40cglmicro.ca (context mfrom, on pmg10.legardeur.net); from=<d.aubry@cglmicro.ca> to=<nancygroulx@aubutgroulx.ca> proto=ESMTP helo=<alt32.smtp-out.videotron.ca>
Nov 15 10:53:03 pmg10 postfix/smtpd[2405904]: disconnect from alt32.smtp-out.videotron.ca[24.53.0.21] ehlo=2 starttls=1 mail=1 rcpt=0/1 rset=1 quit=1 commands=6/7
Nov 15 11:03:59 pmg11 postfix/smtpd[2913688]: connect from alt42.smtp-out.videotron.ca[23.233.128.29]
Nov 15 11:03:59 pmg11 postfix/smtpd[2913688]: NOQUEUE: reject: RCPT from alt42.smtp-out.videotron.ca[23.233.128.29]: 554 5.7.1 <nancygroulx@aubutgroulx.ca>: Recipient address rejected: Rejected by SPF: 23.233.128.29 is not a designated mailserver for d.aubry%40cglmicro.ca (context mfrom, on pmg11.legardeur.net); from=<d.aubry@cglmicro.ca> to=<nancygroulx@aubutgroulx.ca> proto=ESMTP helo=<alt42.smtp-out.videotron.ca>
Nov 15 11:04:59 pmg11 postfix/smtpd[2913688]: disconnect from alt42.smtp-out.videotron.ca[23.233.128.29] ehlo=2 starttls=1 mail=1 rcpt=0/1 rset=1 quit=1 commands=6/7and now here is my setup:


What am I missing?
Thank you.

