Hi All.
Below is my solution for automatically adding proxmox users to Proxmox from an LDAP database.
I wrote this ruby Script as i found it annoying to have to add a user to my LDAP database then have to manually goto 20+ proxmox clusters and add the users manually to the realm as well.
It was not an option for me anymore.
So what the below ruby script will do, It connects to my ldap server and searches for users under proxmox users under groups.
It then loops over members in the list and adds them as users in proxmox under the LDAP realm and then adds them to admin groups.
You will have to edit the settings for DC, usernames and passwords.
Then i use crontab and call every hour to add new users.
Please note im not worried about security as all this is done in private lans and restricted IP addresses, so please be cautious on how you run this.
I also dont do error checking on if a user exists in proxmox, it will just try add it again, proxmox will just not add if already added.
I hope this helps.
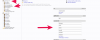
As per above image my ldapserver has an OU (Organisation unit ) called groups
I then have a posix group called proxmoxusers
Distinguished Name: cn=proxmoxusers,ou=groups,dc=example,dc=co,dc=za
1st step. -> On Proxmox Gui
Datacenter -> Permissions -> Authentication -> Add LDAP server
Realm: ldap
Server: <ldap_server_ip_or_hostname>
Base Domain Name : ou=users,dc=example,dc=co,dc=za
User Attribute name : uid
2nd Step -> On Proxmox Host Console
Below is my solution for automatically adding proxmox users to Proxmox from an LDAP database.
I wrote this ruby Script as i found it annoying to have to add a user to my LDAP database then have to manually goto 20+ proxmox clusters and add the users manually to the realm as well.
It was not an option for me anymore.
So what the below ruby script will do, It connects to my ldap server and searches for users under proxmox users under groups.
It then loops over members in the list and adds them as users in proxmox under the LDAP realm and then adds them to admin groups.
You will have to edit the settings for DC, usernames and passwords.
Then i use crontab and call every hour to add new users.
Please note im not worried about security as all this is done in private lans and restricted IP addresses, so please be cautious on how you run this.
I also dont do error checking on if a user exists in proxmox, it will just try add it again, proxmox will just not add if already added.
I hope this helps.

As per above image my ldapserver has an OU (Organisation unit ) called groups
I then have a posix group called proxmoxusers
Distinguished Name: cn=proxmoxusers,ou=groups,dc=example,dc=co,dc=za
1st step. -> On Proxmox Gui
Datacenter -> Permissions -> Authentication -> Add LDAP server
Realm: ldap
Server: <ldap_server_ip_or_hostname>
Base Domain Name : ou=users,dc=example,dc=co,dc=za
User Attribute name : uid
2nd Step -> On Proxmox Host Console
Code:
# apt install git python-mysqldb sshpass nano sudo ruby
# gem install net-ldap
# pveum groupadd admin -comment "System Administrators"
# pveum aclmod / -group admin -role Administrator
# echo "$((RANDOM%60)) */1 * * * root /media/atsscripts/getusercheck_proxmox.rb >/dev/null 2>&1" >> /etc/crontab
Code:
# mkdir /media/atsscripts/
# nano /media/atscripts/getusercheck_proxmox.rb
{
#Add below
#============================================================
#!/usr/bin/env ruby
#gem install net-ldap
require 'rubygems'
require 'net/ldap'
ldap = Net::LDAP.new :host => '<ldapserverip>',
:port => 389,
:auth => {
:method => :simple,
:username => "cn=admin, dc=example, dc=co, dc=za",
:password => "<loginpassword>"
}
filter = Net::LDAP::Filter.eq( "cn", "proxmoxusers*" )
treebase = "ou=groups,dc=example, dc=co, dc=za"
ldap.search( :base => treebase, :filter => filter ) do |entry|
puts "DN: #{entry.dn}"
entry.each do |attribute, values|
p attribute
if "#{attribute}" == "memberuid"
puts " #{attribute}:"
values.each do |value|
system("pveum useradd #{value}@ldap -comment 'Added Via ATS Script'")
system("pveum usermod #{value}@ldap -group admin")
puts " --->#{value}"
end
end
end
end
p ldap.get_operation_result
#============================================================
#Add above
}chmod 770 /media/atscripts/getusercheck_proxmox.rb
Last edited by a moderator:

