I have an odd issue that I am trying to figure out how to resolve.
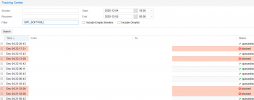
In the logs, my customer got this email (spam / phising)
Dec 2 11:10:20 swarmx1 postfix/smtpd[155817]: connect from winterjoys.com[62.210.130.198]
Dec 2 11:10:21 swarmx1 postfix/smtpd[155817]: Anonymous TLS connection established from winterjoys.com[62.210.130.198]: TLSv1.3 with cipher TLS_AES_256_GCM_SHA384 (256/256 bits) key-exchange X25519 server-signature RSA-PSS (2048 bits) server-digest SHA256
Dec 2 11:10:21 swarmx1 postfix/smtpd[155817]: 80C2C2A037A: client=winterjoys.com[62.210.130.198]
Dec 2 11:10:21 swarmx1 postfix/cleanup[158447]: 80C2C2A037A: message-id=<af6fdc708453bbb79085336094515b577628adbc@winterjoys.com>
Dec 2 11:10:21 swarmx1 postfix/qmgr[513]: 80C2C2A037A: from=<termination@winterjoys.com>, size=49711, nrcpt=1 (queue active)
Dec 2 11:10:21 swarmx1 pmg-smtp-filter[158468]: 2611A85FC7BC6DDCD60: new mail message-id=<af6fdc708453bbb79085336094515b577628adbc@winterjoys.com>#012
Dec 2 11:10:21 swarmx1 postfix/smtpd[155817]: disconnect from winterjoys.com[62.210.130.198] ehlo=2 starttls=1 mail=1 rcpt=1 data=1 quit=1 commands=7
Dec 2 11:10:24 swarmx1 pmg-smtp-filter[158468]: 2611A85FC7BC6DDCD60: SA score=0/5 time=2.110 bayes=0.00 autolearn=no autolearn_force=no hits=BAYES_00(-1.9),DKIM_SIGNED(0.1),DKIM_VALID(-0.1),DKIM_VALID_AU(-0.1),DKIM_VALID_EF(-0.1),HTML_MESSAGE(0.001),RCVD_IN_PSBL(2.7),SPF_HELO_PASS(-0.001),SPF_PASS(-0.001)
Dec 2 11:10:24 swarmx1 postfix/smtpd[158002]: connect from localhost[127.0.0.1]
Dec 2 11:10:24 swarmx1 postfix/smtpd[158002]: 3A31A2A035E: client=localhost[127.0.0.1], orig_client=winterjoys.com[62.210.130.198]
Dec 2 11:10:24 swarmx1 postfix/cleanup[158447]: 3A31A2A035E: message-id=<af6fdc708453bbb79085336094515b577628adbc@winterjoys.com>
Dec 2 11:10:24 swarmx1 postfix/qmgr[513]: 3A31A2A035E: from=<termination@winterjoys.com>, size=50640, nrcpt=1 (queue active)
Dec 2 11:10:24 swarmx1 postfix/smtpd[158002]: disconnect from localhost[127.0.0.1] ehlo=1 xforward=1 mail=1 rcpt=1 data=1 commands=5
Dec 2 11:10:24 swarmx1 pmg-smtp-filter[158468]: 2611A85FC7BC6DDCD60: accept mail to <info@domain.ca> (3A31A2A035E) (rule: default-accept)
Dec 2 11:10:24 swarmx1 pmg-smtp-filter[158468]: 2611A85FC7BC6DDCD60: processing time: 2.338 seconds (2.11, 0.191, 0)
Dec 2 11:10:24 swarmx1 postfix/lmtp[157876]: 80C2C2A037A: to=<info@domain.ca>, relay=127.0.0.1[127.0.0.1]:10024, delay=2.8, delays=0.48/0/0/2.3, dsn=2.5.0, status=sent (250 2.5.0 OK (2611A85FC7BC6DDCD60))
Dec 2 11:10:24 swarmx1 postfix/qmgr[513]: 80C2C2A037A: removed
Dec 2 11:10:24 swarmx1 postfix/smtp[158385]: 3A31A2A035E: to=<info@domain.ca>, relay=192.168.11.221[192.168.11.221]:25, delay=0.07, delays=0.01/0/0.05/0.02, dsn=2.0.0, status=sent (250 Mail queued for delivery)
Dec 2 11:10:24 swarmx1 postfix/qmgr[513]: 3A31A2A035E: removed
The "reply to" email is set to: invoice@swarmx1.mailhive.ca
swarmx1 and swarmx2 in this case are my PMG servers. How can I block emails like this getting through to customers? The fact that the reply to is a legit domain for the PMG servers is a little alarming. Can anyone thing of a way to stop this sort of email from coming in? Blocking the main domain spamming :winterjoys.com would be one thing but its a temporary solution. Ideally, I'd like to block anything that has a reply to that points back to these servers.
Hopefully this makes sense. Thanks!
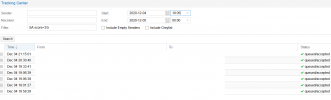
In the logs, my customer got this email (spam / phising)
Dec 2 11:10:20 swarmx1 postfix/smtpd[155817]: connect from winterjoys.com[62.210.130.198]
Dec 2 11:10:21 swarmx1 postfix/smtpd[155817]: Anonymous TLS connection established from winterjoys.com[62.210.130.198]: TLSv1.3 with cipher TLS_AES_256_GCM_SHA384 (256/256 bits) key-exchange X25519 server-signature RSA-PSS (2048 bits) server-digest SHA256
Dec 2 11:10:21 swarmx1 postfix/smtpd[155817]: 80C2C2A037A: client=winterjoys.com[62.210.130.198]
Dec 2 11:10:21 swarmx1 postfix/cleanup[158447]: 80C2C2A037A: message-id=<af6fdc708453bbb79085336094515b577628adbc@winterjoys.com>
Dec 2 11:10:21 swarmx1 postfix/qmgr[513]: 80C2C2A037A: from=<termination@winterjoys.com>, size=49711, nrcpt=1 (queue active)
Dec 2 11:10:21 swarmx1 pmg-smtp-filter[158468]: 2611A85FC7BC6DDCD60: new mail message-id=<af6fdc708453bbb79085336094515b577628adbc@winterjoys.com>#012
Dec 2 11:10:21 swarmx1 postfix/smtpd[155817]: disconnect from winterjoys.com[62.210.130.198] ehlo=2 starttls=1 mail=1 rcpt=1 data=1 quit=1 commands=7
Dec 2 11:10:24 swarmx1 pmg-smtp-filter[158468]: 2611A85FC7BC6DDCD60: SA score=0/5 time=2.110 bayes=0.00 autolearn=no autolearn_force=no hits=BAYES_00(-1.9),DKIM_SIGNED(0.1),DKIM_VALID(-0.1),DKIM_VALID_AU(-0.1),DKIM_VALID_EF(-0.1),HTML_MESSAGE(0.001),RCVD_IN_PSBL(2.7),SPF_HELO_PASS(-0.001),SPF_PASS(-0.001)
Dec 2 11:10:24 swarmx1 postfix/smtpd[158002]: connect from localhost[127.0.0.1]
Dec 2 11:10:24 swarmx1 postfix/smtpd[158002]: 3A31A2A035E: client=localhost[127.0.0.1], orig_client=winterjoys.com[62.210.130.198]
Dec 2 11:10:24 swarmx1 postfix/cleanup[158447]: 3A31A2A035E: message-id=<af6fdc708453bbb79085336094515b577628adbc@winterjoys.com>
Dec 2 11:10:24 swarmx1 postfix/qmgr[513]: 3A31A2A035E: from=<termination@winterjoys.com>, size=50640, nrcpt=1 (queue active)
Dec 2 11:10:24 swarmx1 postfix/smtpd[158002]: disconnect from localhost[127.0.0.1] ehlo=1 xforward=1 mail=1 rcpt=1 data=1 commands=5
Dec 2 11:10:24 swarmx1 pmg-smtp-filter[158468]: 2611A85FC7BC6DDCD60: accept mail to <info@domain.ca> (3A31A2A035E) (rule: default-accept)
Dec 2 11:10:24 swarmx1 pmg-smtp-filter[158468]: 2611A85FC7BC6DDCD60: processing time: 2.338 seconds (2.11, 0.191, 0)
Dec 2 11:10:24 swarmx1 postfix/lmtp[157876]: 80C2C2A037A: to=<info@domain.ca>, relay=127.0.0.1[127.0.0.1]:10024, delay=2.8, delays=0.48/0/0/2.3, dsn=2.5.0, status=sent (250 2.5.0 OK (2611A85FC7BC6DDCD60))
Dec 2 11:10:24 swarmx1 postfix/qmgr[513]: 80C2C2A037A: removed
Dec 2 11:10:24 swarmx1 postfix/smtp[158385]: 3A31A2A035E: to=<info@domain.ca>, relay=192.168.11.221[192.168.11.221]:25, delay=0.07, delays=0.01/0/0.05/0.02, dsn=2.0.0, status=sent (250 Mail queued for delivery)
Dec 2 11:10:24 swarmx1 postfix/qmgr[513]: 3A31A2A035E: removed
The "reply to" email is set to: invoice@swarmx1.mailhive.ca
swarmx1 and swarmx2 in this case are my PMG servers. How can I block emails like this getting through to customers? The fact that the reply to is a legit domain for the PMG servers is a little alarming. Can anyone thing of a way to stop this sort of email from coming in? Blocking the main domain spamming :winterjoys.com would be one thing but its a temporary solution. Ideally, I'd like to block anything that has a reply to that points back to these servers.
Hopefully this makes sense. Thanks!