Yesterday was great. But I knew I needed to replace the physical node 3 of my cluster with a qdevice. Today was that day.
I had some small problem somewhere along the way of adding the qdevice, but it worked easily enough.
Then suddenly my replication jobs from node 'pve' to 'pve2' started failing with SSH errors.
I went down the rabbit hole here:
https://forum.proxmox.com/threads/s...to-bypass-ssh-known_hosts-bug-s.137809/page-2
@esi_y
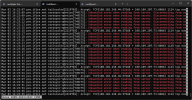
So as of now, the issue is from pve when issuing 'ssh pve2' I am connected with pve again, not with pve2. This worked fine yesterday. Not sure at what point exactly that it stopped.
The cluster has quorum.
Praying that @esi_y will help me over the last hurdle here, my head hurts!
I had some small problem somewhere along the way of adding the qdevice, but it worked easily enough.
Then suddenly my replication jobs from node 'pve' to 'pve2' started failing with SSH errors.
I went down the rabbit hole here:
https://forum.proxmox.com/threads/s...to-bypass-ssh-known_hosts-bug-s.137809/page-2
@esi_y
So as of now, the issue is from pve when issuing 'ssh pve2' I am connected with pve again, not with pve2. This worked fine yesterday. Not sure at what point exactly that it stopped.
The cluster has quorum.
Praying that @esi_y will help me over the last hurdle here, my head hurts!