Hello All!
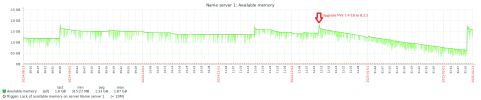
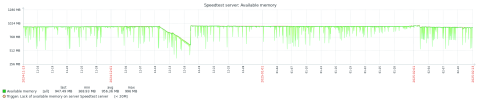
I have been experiencing some LXC with small memory allocation stops, randomly dies silently without any trace of cause. Watching over time, I found that the most probably reason is out of memory. Allocating more memory allows it to run longer, but it fails anyway. When I try to find out where the memory lost, I found that "shared" grows and grows until reach OOM condition.
The result my investigation is very courious, follow the sequence:
1. When container starts, it has tmpfs mount at
2. Systemd-journald puts journal files to
3. Grow of journals depends of app and it's loging mode, therefore when LXC run something that never use journald extensively, it may run without problem. But if the app use journald it lead to constant growith of tmpfs usage.
4. However, tmpfs really allocated within container memory limit!
5. Then, OOM condition is just a matter of time if LCX memory allocacion is less then 5% of physical memory size and there extensive use of journald inside LXC.
So, I have some LXCs with 1-2GB allocation for lightweigt apps that really use 150-200Mb of memory, but these apps use journald to log. With 6GB default journald log limit it goes to OOM condition, just a matter of time.
This issue has a very simple workaround: to set journald runtime log size limit in
and restart
This should force Journald to keep tmpfs usage within 128M (or whatever your configure) and flush logs to disk, where another 10% to filesystem size limit should apply.
Questons: is it a bug of just behavior by design? Should PVE set tmpfs size accourdng to LXC memory allocation? Is there a way to manage it globally, without taking care about journald config in each LXC?
I have been experiencing some LXC with small memory allocation stops, randomly dies silently without any trace of cause. Watching over time, I found that the most probably reason is out of memory. Allocating more memory allows it to run longer, but it fails anyway. When I try to find out where the memory lost, I found that "shared" grows and grows until reach OOM condition.
The result my investigation is very courious, follow the sequence:
1. When container starts, it has tmpfs mount at
/run and the size of tmpfs is set to a half of physical server physical memory size, not the size of LXC allocated memory. In my case the tmpfs size is 63 GB (server has 128GB) while container has 2GB allocation.2. Systemd-journald puts journal files to
/run/log/journal (tmpfs!), with default journal size limit is 10% of the filesystem size (my case - 6.3GB limit)3. Grow of journals depends of app and it's loging mode, therefore when LXC run something that never use journald extensively, it may run without problem. But if the app use journald it lead to constant growith of tmpfs usage.
4. However, tmpfs really allocated within container memory limit!
5. Then, OOM condition is just a matter of time if LCX memory allocacion is less then 5% of physical memory size and there extensive use of journald inside LXC.
So, I have some LXCs with 1-2GB allocation for lightweigt apps that really use 150-200Mb of memory, but these apps use journald to log. With 6GB default journald log limit it goes to OOM condition, just a matter of time.
This issue has a very simple workaround: to set journald runtime log size limit in
/etc/systemd/journald.conf
Code:
RuntimeMaxUse=128Msystemd-journaldThis should force Journald to keep tmpfs usage within 128M (or whatever your configure) and flush logs to disk, where another 10% to filesystem size limit should apply.
Questons: is it a bug of just behavior by design? Should PVE set tmpfs size accourdng to LXC memory allocation? Is there a way to manage it globally, without taking care about journald config in each LXC?
Last edited: