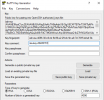
/usr/sbin/shutdown is probably what you are looking for. You typed
/etc/ 
This just makes it possible for the user to issue the command without having to authenticate with the password.
Before you can do any of that, you have to connect to the machine, e.g. via SSH. SSH creates a connection from your Windows VM to your Proxmox host. To establish this connection, it usually needs a username and a password (so pretty much like everywhere else) but like
@Dunuin said, setting up public-private-key authentication is generally recommended and a lot more secure. (and also means you won't have to type in the password manually!)
Once the connection is established, you can then issue the command. This is where the entry in the sudoers file comes into play.