Cheers Proxmox-Community,
i've started using proxmox about two weeks ago and judging by what i've seen so far: i like it.
Currently i' struggeling with creating a vm-internal lab LAN. I've searech and tried some guieds / settings but cant seem to find the right thing for me.
To be able to evaluate changes without impacting the productiv VMs i would love to clone the productiv machines an put them an a "lab-LAN".
Whats my goal?
creating a LAB-LAN where VMs on it can communicate with each other without impacting productiv LAN
Functions required within that LAN:
DHCP, DNS, PXE(provided by VMs within that net)
What have i done so far?
Does anybody know a guide which suites my plan or can tell me what i'm doing wrong in my SDN?
i've started using proxmox about two weeks ago and judging by what i've seen so far: i like it.
Currently i' struggeling with creating a vm-internal lab LAN. I've searech and tried some guieds / settings but cant seem to find the right thing for me.
To be able to evaluate changes without impacting the productiv VMs i would love to clone the productiv machines an put them an a "lab-LAN".
Whats my goal?
creating a LAB-LAN where VMs on it can communicate with each other without impacting productiv LAN
Functions required within that LAN:
DHCP, DNS, PXE(provided by VMs within that net)
What have i done so far?
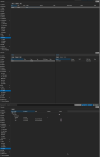
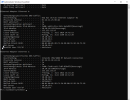
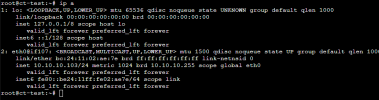
- created a SDN (Zone + VNet + Subnet with DHCP), attached a VM & CT to that VNet. When i check IPAM the both listed with an ipaddress. Checking on the interfaces from the VM/CT they only got APIPA addresses.
- tried it on a OVSbridge without any physical IF by adding a Container which handles DHCP. (this failed because i'm lacking knowledge configuring dnsmasq)
Does anybody know a guide which suites my plan or can tell me what i'm doing wrong in my SDN?