I'm sure this is going to be a painfully beginner question and I apologize from the start:
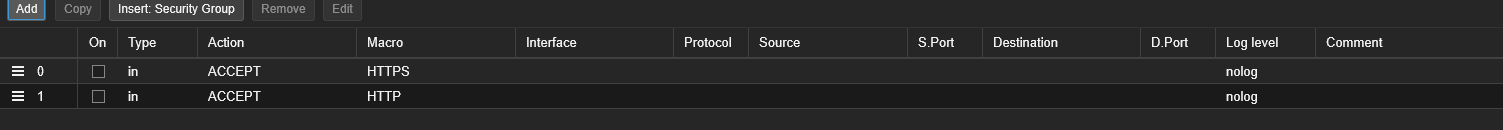
I'm attempting to expose a single VM to 8080 and 443. Unfortunately, networking is not my strong suit. I have two rules assigned to it, set up as shown here:

(and then for HTTPS the source port is set to 443, but the rest of the screenshot is the same)
This has not exposed the webserver (I'm attempting to run SANS's dshield honeypot, its status script is what's reporting the failure).
I enabled FIREWALL=YES on the VM; it warned the Firewall was not enabled at the Datacenter level, so I then did that. All this achieved was apparently a DENY-ALL default rule that has locked me out of the console. This leads me to two questions:
- How do I disable the datacenter level firewall directly from the host?
- How do I properly set a single VM on the host to be exposed to the internet?
I'm attempting to expose a single VM to 8080 and 443. Unfortunately, networking is not my strong suit. I have two rules assigned to it, set up as shown here:

(and then for HTTPS the source port is set to 443, but the rest of the screenshot is the same)
This has not exposed the webserver (I'm attempting to run SANS's dshield honeypot, its status script is what's reporting the failure).
I enabled FIREWALL=YES on the VM; it warned the Firewall was not enabled at the Datacenter level, so I then did that. All this achieved was apparently a DENY-ALL default rule that has locked me out of the console. This leads me to two questions:
- How do I disable the datacenter level firewall directly from the host?
- How do I properly set a single VM on the host to be exposed to the internet?