Hello! As title states, I'm using a Simple SDN zone with auto dhcp enabled, dnsmasq installed, basically everything working. HOWEVER, when I enable the node-level firewall, dhcp stops working entirely. Datacentre firewall doesn't effect dhcp.
I have the rules set up from the guide on both a datacentre and a node-level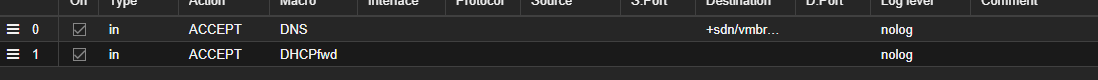
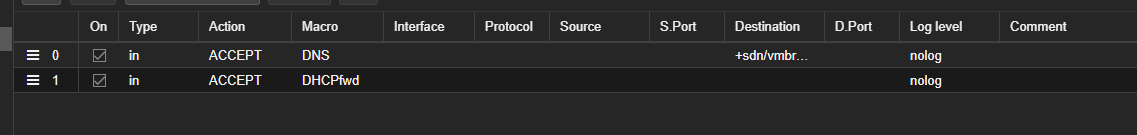
(These are screenshots from the Datacentre firewall, and then the node firewall)
the VNet is called vmbr100, so the DNS rule is set to point to the SDN zones gateway.
What I'm trying to do is isolate the simple SDN zone so it doesn't have access to the LAN it's SNAT'd behind.. if that makes sense.
Thanks If there's any questions I can answer to help myself out, please let me know.
If there's any questions I can answer to help myself out, please let me know.
I have the rules set up from the guide on both a datacentre and a node-level


(These are screenshots from the Datacentre firewall, and then the node firewall)
the VNet is called vmbr100, so the DNS rule is set to point to the SDN zones gateway.
What I'm trying to do is isolate the simple SDN zone so it doesn't have access to the LAN it's SNAT'd behind.. if that makes sense.
Thanks

