I want all my VMs to go through my firewall VM. I know I need to bridge all of them but when I check the network on the host it shows the pve IP I chose during install.
Do I need to add a new Linux Bridge for every VM or just use the same vmbr0 for all of them and proxmox will do the rest and route/switch between them?
The only thing that confuses me is the pve's IP assignment on that vmbr0 bridge.
I'm thinking of this solution - leave vmbr0 (pve's bridge) untouched, add a new bridge vmbr1 and make all the VMs use it as a "switch", assign this new bridge as a network device on the pfSense VM and I think it should work, but then how do I also bridge the pve host through pfsense? Add its bridge as a network device too in the pfSense VM?
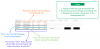
My network looks like this:

Thank you,
Do I need to add a new Linux Bridge for every VM or just use the same vmbr0 for all of them and proxmox will do the rest and route/switch between them?
The only thing that confuses me is the pve's IP assignment on that vmbr0 bridge.
I'm thinking of this solution - leave vmbr0 (pve's bridge) untouched, add a new bridge vmbr1 and make all the VMs use it as a "switch", assign this new bridge as a network device on the pfSense VM and I think it should work, but then how do I also bridge the pve host through pfsense? Add its bridge as a network device too in the pfSense VM?
My network looks like this:

Thank you,