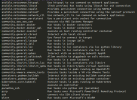
As far as I can see, Proxmox VE is currently only partially configurable through community provided Ansible modules. (See below)
Inventory Plugins:
Modules:
Are there any plans to create an official collection in order to make Proxmox VE fully configurable through Ansible?
VMware already provides such a collection. It would be awesome, if Proxmox provided one too.
I already have started to implement a few modules making use of the Proxmox VE API. I would gladly contribute my stub to an official collection.
Inventory Plugins:
Modules:
- proxmox
- proxmox_domain_info
- proxmox_group_info
- proxmox_kvm
- proxmox_nic
- proxmox_snap
- proxmox_storage_info
- proxmox_tasks_info
- proxmox_template
- proxmox_user_info
Are there any plans to create an official collection in order to make Proxmox VE fully configurable through Ansible?
VMware already provides such a collection. It would be awesome, if Proxmox provided one too.
I already have started to implement a few modules making use of the Proxmox VE API. I would gladly contribute my stub to an official collection.