without pcie_acs_overrideTry without the pcie_acs_override and list the IOMMU groups then. Also, you have the 'hostpci' device configured 4 times in your config, one time is enough if you enable "All functions" in the GUI.
the IOMMU grouping is the same:
Code:
IOMMU Group 28:
21:00.0 VGA compatible controller [0300]: NVIDIA Corporation TU102 [GeForce RTX 2080 Ti] [10de:1e04] (rev a1)
21:00.1 Audio device [0403]: NVIDIA Corporation TU102 High Definition Audio Controller [10de:10f7] (rev a1)
21:00.2 USB controller [0c03]: NVIDIA Corporation TU102 USB 3.1 Controller [10de:1ad6] (rev a1)
21:00.3 Serial bus controller [0c80]: NVIDIA Corporation TU102 UCSI Controller [10de:1ad7] (rev a1)"have the 'hostpci' device configured 4 times in your config"
I thought these four time is because four devices that I can see in IOMMU group 28 (all from NVIDIA 2080Ti)
(I follow a guide here, he added two and have all function checked https://www.reddit.com/r/homelab/comments/b5xpua/the_ultimate_beginners_guide_to_gpu_passthrough/)
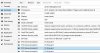
like the sreenshot below, with all function checked for all four device.
I did add them in GUI not by CLI.
If I add just the first one and check all functions. It still has the same error: group 28 is not viable.
The below has only the first one PCI passthrough.
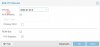
With only one pci passthrough
Code:
qm showcmd 500 --pretty > /tmp/qm.shroot@mars:~# cat /tmp/qm.sh/usr/bin/kvm \
-id 500 \
-name Win10Edu-1909-2080Ti \
-chardev 'socket,id=qmp,path=/var/run/qemu-server/500.qmp,server,nowait' \
-mon 'chardev=qmp,mode=control' \
-chardev 'socket,id=qmp-event,path=/var/run/qmeventd.sock,reconnect=5' \
-mon 'chardev=qmp-event,mode=control' \
-pidfile /var/run/qemu-server/500.pid \
-daemonize \
-smbios 'type=1,uuid=51b7e8ff-ae21-45e2-942a-c236379bbd62' \
-drive 'if=pflash,unit=0,format=raw,readonly,file=/usr/share/pve-edk2-firmware//OVMF_CODE.fd' \
-drive 'if=pflash,unit=1,format=raw,id=drive-efidisk0,size=131072,file=/dev/zvol/nvmepool/vm-500-disk-1' \
-smp '32,sockets=1,cores=32,maxcpus=32' \
-nodefaults \
-boot 'menu=on,strict=on,reboot-timeout=1000,splash=/usr/share/qemu-server/bootsplash.jpg' \
-vga none \
-nographic \
-no-hpet \
-cpu 'host,hv_ipi,hv_relaxed,hv_reset,hv_runtime,hv_spinlocks=0x1fff,hv_stimer,hv_synic,hv_time,hv_vapic,hv_vpindex,+ibpb,kvm=off,+kvm_pv_eoi,+kvm_pv_unhalt,-pcid' \
-m 32768 \
-object 'memory-backend-ram,id=ram-node0,size=32768M' \
-numa 'node,nodeid=0,cpus=0-31,memdev=ram-node0' \
-readconfig /usr/share/qemu-server/pve-q35-4.0.cfg \
-device 'vmgenid,guid=c1d954f9-87b9-47cb-83f4-7a5505137199' \
-device 'usb-tablet,id=tablet,bus=ehci.0,port=1' \
-device 'vfio-pci,host=0000:21:00.0,id=hostpci0.0,bus=ich9-pcie-port-1,addr=0x0.0,multifunction=on' \
-device 'vfio-pci,host=0000:21:00.1,id=hostpci0.1,bus=ich9-pcie-port-1,addr=0x0.1' \
-device 'vfio-pci,host=0000:21:00.2,id=hostpci0.2,bus=ich9-pcie-port-1,addr=0x0.2' \
-device 'vfio-pci,host=0000:21:00.3,id=hostpci0.3,bus=ich9-pcie-port-1,addr=0x0.3' \
-chardev 'socket,path=/var/run/qemu-server/500.qga,server,nowait,id=qga0' \
-device 'virtio-serial,id=qga0,bus=pci.0,addr=0x8' \
-device 'virtserialport,chardev=qga0,name=org.qemu.guest_agent.0' \
-iscsi 'initiator-name=iqn.1993-08.org.debian:01:baecad992489' \
-device 'virtio-scsi-pci,id=scsihw0,bus=pci.0,addr=0x5' \
-drive 'file=/dev/zvol/nvmepool/vm-500-disk-0,if=none,id=drive-scsi0,cache=writeback,discard=on,format=raw,aio=threads,detect-zeroes=unmap' \
-device 'scsi-hd,bus=scsihw0.0,channel=0,scsi-id=0,lun=0,drive=drive-scsi0,id=scsi0,rotation_rate=1,bootindex=100' \
-device 'ahci,id=ahci0,multifunction=on,bus=pci.0,addr=0x7' \
-drive 'file=/mnt/pve/network-neoproxmox/template/iso/en_windows_10_consumer_editions_version_1909_x64_dvd_be09950e.iso,if=none,id=drive-sata2,media=cdrom,aio=threads' \
-device 'ide-cd,bus=ahci0.2,drive=drive-sata2,id=sata2,bootindex=200' \
-drive 'file=/mnt/pve/network-neoproxmox/template/iso/virtio-win-0.1.185.iso,if=none,id=drive-sata3,media=cdrom,aio=threads' \
-device 'ide-cd,bus=ahci0.3,drive=drive-sata3,id=sata3,bootindex=201' \
-netdev 'type=tap,id=net0,ifname=tap500i0,script=/var/lib/qemu-server/pve-bridge,downscript=/var/lib/qemu-server/pve-bridgedown,vhost=on' \
-device 'virtio-net-pci,mac=3E:80:D5:FD:81:D2,netdev=net0,bus=pci.0,addr=0x12,id=net0,bootindex=300' \
-rtc 'driftfix=slew,base=localtime' \
-machine 'type=q35+pve0' \
-global 'kvm-pit.lost_tick_policy=discard' \
-machine 'type=q35,kernel_irqchip=on'
root@mars:~# sh /tmp/qm.shkvm: -device vfio-pci,host=0000:21:00.0,id=hostpci0.0,bus=ich9-pcie-port-1,addr=0x0.0,multifunction=on: vfio 0000:21:00.0: group 28 is not viable
Please ensure all devices within the iommu_group are bound to their vfio bus driver.
Last edited:

