Hello,
I use the firewall built into Proxmox which is great.
On the private network (172.16.10.x ) the firewall works and blocks what is not explicitly opened (Input Policy: DROP, OUTPUT Policy: ACCEPT), but when I use a public IP, the firewall totally ignores the rules and all traffic on the pub-ip goes unrestricted (but the private IP is still filtered).
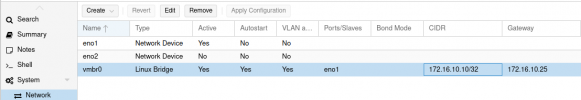
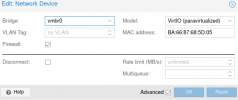
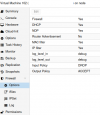
Here is my network configuration on the VM side :
For example, if I install a webserver and listen on both 201.40.31.7:80 and 172.16.10.11:80, If I dont allow HTTP traffic on the proxmox firewall, it will not work on private ip (wich is great!) but on the public ip, whatever the setting is, it will ignore the firewall and work in any case
Private IP is on the VLAN 50
Public IP are on the VLAN 100
The firewall is activated cluster-wide, on each host and on each VM (and on the network card of the vm ofc!)
I also tried to put INPUT Policy: DROP and OUTPUT Policy: DROP, the trafic is dropped on the private network, but the public still ip pass through.
Did i forget something ?
I hope somebody can help me!
Regards
I use the firewall built into Proxmox which is great.
On the private network (172.16.10.x ) the firewall works and blocks what is not explicitly opened (Input Policy: DROP, OUTPUT Policy: ACCEPT), but when I use a public IP, the firewall totally ignores the rules and all traffic on the pub-ip goes unrestricted (but the private IP is still filtered).
Here is my network configuration on the VM side :
Code:
admin@vm:~$ cat /etc/network/interfaces
auto lo
iface lo inet loopback
auto eth0
iface eth0 inet static
address 172.16.10.11/24
dns-nameservers 172.16.10.25 1.1.1.1
auto eth0.100
iface eth0.100 inet static
address 201.40.31.7/32
gateway 201.40.31.28For example, if I install a webserver and listen on both 201.40.31.7:80 and 172.16.10.11:80, If I dont allow HTTP traffic on the proxmox firewall, it will not work on private ip (wich is great!) but on the public ip, whatever the setting is, it will ignore the firewall and work in any case
PVE nodes does not have public IPs, only private IPs (172.16.10.x), every node use a gateway on the private network (172.16.10.25) to reach internet.
All VMs have a private IP (172.16.10.x), and some have a public IP.
Private IP is on the VLAN 50
Public IP are on the VLAN 100
The firewall is activated cluster-wide, on each host and on each VM (and on the network card of the vm ofc!)
Code:
pve-firewall status
Status: enabled/runningI also tried to put INPUT Policy: DROP and OUTPUT Policy: DROP, the trafic is dropped on the private network, but the public still ip pass through.
Did i forget something ?
I hope somebody can help me!
Regards