Hey all. I just did a 3.4 -> 4.0 upgrade. The upgrade itself went really well. However I am running into an issue I can't seem to pin down.
We are a bit odd as we run one large VM within a 3 node HA stack. I am finding that when I get above 7-10 cores I am running into a very odd issue. While the VM is booting the KVM process on the host starts eating CPU cycles. So bad that sometimes it causes an NMI on the host. This happens while the guest is booting and setting up the kvm-clock per CPU.
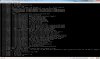
The guest says the following
Total of 46 processors activated (211355.09 BogoMIPS)
The KVM process on the host is currently running at 4000+ %CPU on top. Sometimes it will manage to get the VM up and sometimes it will cause the host to NMI. Once the guest is up, load drops and all is well.
The hardware is HP DL380 Gen9's. The guest OS is CentOS 6.6 with 320G of ram and 46 vCPU's. Virtio drivers.
I already did a complete shell swap to ensure it wasn't a hardware issue. I can reproduce the issue on multiple nodes.
We are a bit odd as we run one large VM within a 3 node HA stack. I am finding that when I get above 7-10 cores I am running into a very odd issue. While the VM is booting the KVM process on the host starts eating CPU cycles. So bad that sometimes it causes an NMI on the host. This happens while the guest is booting and setting up the kvm-clock per CPU.
The guest says the following
Total of 46 processors activated (211355.09 BogoMIPS)
The KVM process on the host is currently running at 4000+ %CPU on top. Sometimes it will manage to get the VM up and sometimes it will cause the host to NMI. Once the guest is up, load drops and all is well.
The hardware is HP DL380 Gen9's. The guest OS is CentOS 6.6 with 320G of ram and 46 vCPU's. Virtio drivers.
I already did a complete shell swap to ensure it wasn't a hardware issue. I can reproduce the issue on multiple nodes.
Last edited: