Hello.
After server reboot I received a MAC abuse notification from Hetzner.
Looking the networks device, now I have found this 2 mac in 2fwbr.
I have on vmbr0 opnesense with vmbr1 and vmbr2 as private LAN.
Others vps and xlc are directly connected on the vmbr0 with separate public ip's and dedicated MAC address relased from hetzner and someone at the same time on the vmbr2 private LAN
Why this happen?!?
> Unallowed MACs:
> 3a:3e:f1:e2:5f:2b - (code line 8 and 10)
> ea:9b:09:ea:b3:4f - (code line 12 and 14)
After server reboot I received a MAC abuse notification from Hetzner.
Looking the networks device, now I have found this 2 mac in 2fwbr.
I have on vmbr0 opnesense with vmbr1 and vmbr2 as private LAN.
Others vps and xlc are directly connected on the vmbr0 with separate public ip's and dedicated MAC address relased from hetzner and someone at the same time on the vmbr2 private LAN
Why this happen?!?
> Unallowed MACs:
> 3a:3e:f1:e2:5f:2b - (code line 8 and 10)
> ea:9b:09:ea:b3:4f - (code line 12 and 14)

1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: enp2s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast master vmbr0 state UP group default qlen 1000
link/ether d4:3d:7e:d8:bd:c5 brd ff:ff:ff:ff:ff:ff
3: vmbr0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether d4:3d:7e:d8:bd:c5 brd ff:ff:ff:ff:ff:ff
inet xxxx.xx.xx.35 peer xxx.xx.xx.33/32 brd xxx.xx.xxx.63 scope global vmbr0
valid_lft forever preferred_lft forever
inet6 fe80::d63d:7eff:fed8:bdc5/64 scope link
valid_lft forever preferred_lft forever
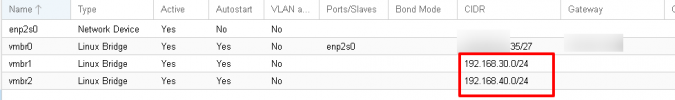
4: vmbr1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether aa:20:df:e2:84:9c brd ff:ff:ff:ff:ff:ff
inet 192.168.30.0/24 brd 192.168.30.255 scope global vmbr1
valid_lft forever preferred_lft forever
inet6 fe80::78e5:9eff:fee4:5fa2/64 scope link
valid_lft forever preferred_lft forever
5: vmbr2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UNKNOWN group default qlen 1000
link/ether b2:00:40:0b:c1:b6 brd ff:ff:ff:ff:ff:ff
inet 192.168.40.0/24 brd 192.168.40.255 scope global vmbr2
valid_lft forever preferred_lft forever
inet6 fe80::b000:40ff:fe0b:c1b6/64 scope link
valid_lft forever preferred_lft forever
6: tailscale0: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1280 qdisc pfifo_fast state UNKNOWN group default qlen 500
link/none
inet xxx.xx.xx.74/32 scope global tailscale0
valid_lft forever preferred_lft forever
inet6 fd7a:115c:a1e0:ab12:4843:cd96:624c:194a/128 scope global
valid_lft forever preferred_lft forever
inet6 fe80::32c0:fb93:8c30:7cf9/64 scope link stable-privacy
valid_lft forever preferred_lft forever
7: veth114i0@if2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master fwbr114i0 state UP group default qlen 1000
link/ether fe:cd:09:f0:2b:e2 brd ff:ff:ff:ff:ff:ff link-netnsid 0
8: fwbr114i0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether [B]3a:3e:f1:e2:5f:2b[/B] brd ff:ff:ff:ff:ff:ff
9: fwpr114p0@fwln114i0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master vmbr0 state UP group default qlen 1000
link/ether b6:8c:4d:12:53:8c brd ff:ff:ff:ff:ff:ff
10: fwln114i0@fwpr114p0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master fwbr114i0 state UP group default qlen 1000
link/ether [B]3a:3e:f1:e2:5f:2b[/B] brd ff:ff:ff:ff:ff:ff
11: tap200i0: <BROADCAST,MULTICAST,PROMISC,UP,LOWER_UP> mtu 1500 qdisc mq master fwbr200i0 state UNKNOWN group default qlen 1000
link/ether c2:e8:08:25:fb:d1 brd ff:ff:ff:ff:ff:ff
12: fwbr200i0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether [B]ea:9b:09:ea:b3:4f[/B] brd ff:ff:ff:ff:ff:ff
13: fwpr200p0@fwln200i0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master vmbr0 state UP group default qlen 1000
link/ether ea:68:35:62:f1:5f brd ff:ff:ff:ff:ff:ff
14: fwln200i0@fwpr200p0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master fwbr200i0 state UP group default qlen 1000
link/ether [B]ea:9b:09:ea:b3:4f [/B]brd ff:ff:ff:ff:ff:ff
20: tap100i0: <BROADCAST,MULTICAST,PROMISC,UP,LOWER_UP> mtu 1500 qdisc mq master fwbr100i0 state UNKNOWN group default qlen 1000
link/ether aa:b0:74:ab:f4:e4 brd ff:ff:ff:ff:ff:ff
21: fwbr100i0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether c2:e1:f1:3f:b4:ce brd ff:ff:ff:ff:ff:ff
22: fwpr100p0@fwln100i0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master vmbr0 state UP group default qlen 1000
link/ether 76:38:69:53:7f:51 brd ff:ff:ff:ff:ff:ff
23: fwln100i0@fwpr100p0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master fwbr100i0 state UP group default qlen 1000
link/ether c2:e1:f1:3f:b4:ce brd ff:ff:ff:ff:ff:ff
24: tap100i1: <BROADCAST,MULTICAST,PROMISC,UP,LOWER_UP> mtu 1500 qdisc mq master vmbr1 state UNKNOWN group default qlen 1000
link/ether aa:20:df:e2:84:9c brd ff:ff:ff:ff:ff:ff
Last edited:

