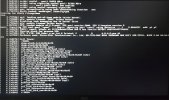
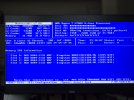
Edit: My problem was faulty ram sticks.
So I recently installed the latest version of proxmox with ZFS raid 1 on a new machine with the following specs:
I attach the output when that happened. I apologize for the pics being shit, since I don't have another way I can think of getting the output without using my phone camera.
So I recently installed the latest version of proxmox with ZFS raid 1 on a new machine with the following specs:
- Mobo: MSI MAG B550 Tomahawk Max Wifi
- Cpu: AMD RYZEN 7 5700X
- Cpu Fan: Noctua NH-D9L
- Ram: HYPERX Fury 32GB (4x8GB) DDR4 2400MHz
- Gpu: Nivida Gtx 1030
- Storage: SanDisk SSD PLUS 240GB
- 2nd Storage: Western Digital 240GB WD Green Internal SSD
- Psu: EVGA 650 BP, 80+ BRONZE 650W
I attach the output when that happened. I apologize for the pics being shit, since I don't have another way I can think of getting the output without using my phone camera.
Attachments
Last edited: