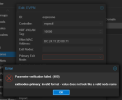
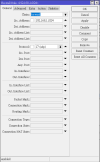
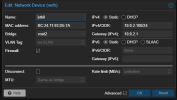
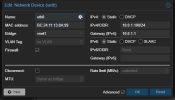
I already changed this option "datacenter" to "traditional" a couple of days ago, when I first saw that option but wasn't doing anything. I will try again in a sec.
A ping from node2 to node1:
I don't know, but this has to be enough, even the proxmox cluster is running with this.
Do you see anything else in the logs?
Is it possible, that bgp or whatever uses ipv6 for something and if it isn't configured correctly, then it dies silently like this? Otherwise this must be a bug, I mean, today I updated to the latest proxmox packages and it's always the same behaviour. EVPN simply does not work, not out of the box, not at all for me. Do you use it with older Proxmox package versions?
A ping from node2 to node1:
Code:
64 bytes from 88.XX.XX.XX: icmp_seq=1 ttl=61 time=0.391 ms
64 bytes from 88.XX.XX.XX: icmp_seq=2 ttl=61 time=0.459 ms
64 bytes from 88.XX.XX.XX: icmp_seq=3 ttl=61 time=0.477 msI don't know, but this has to be enough, even the proxmox cluster is running with this.
Do you see anything else in the logs?
Is it possible, that bgp or whatever uses ipv6 for something and if it isn't configured correctly, then it dies silently like this? Otherwise this must be a bug, I mean, today I updated to the latest proxmox packages and it's always the same behaviour. EVPN simply does not work, not out of the box, not at all for me. Do you use it with older Proxmox package versions?
Last edited: