Hi SpiritI have fixed the mtu on ovsint port, I have resent:
http://odisoweb1.odiso.net/libpve-network-perl_0.4-4_all.deb
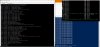
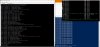
After loading above I see ln_vnet4040 is still mtu of 1500
Code:
root@pve00:~# cat /etc/network/interfaces.d/sdn
#version:57
auto ln_vnet4040
iface ln_vnet4040
ovs_type OVSIntPort
ovs_bridge vmbr0
ovs_options vlan_mode=dot1q-tunnel tag=4040
auto vmbr0
iface vmbr0
ovs_ports ln_vnet4040
auto vnet4040
iface vnet4040
bridge_ports ln_vnet4040
bridge_stp off
bridge_fd 0
bridge-vlan-aware yes
bridge-vids 2-4094
mtu 9000
root@pve00:~# cat /etc/pve/sdn/zones.cfg
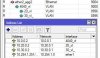
vlan: zvlan
bridge vmbr0
mtu 9000
root@pve00:~# cat /etc/pve/sdn/vnets.cfg
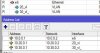
vnet: vnet4040
tag 4040
zone zvlan
vlanaware 1
root@pve00:~# ovs-vsctl show
82d024d1-224b-4fa9-a4ad-c596570ce3d9
Bridge "vmbr0"
Port "vlan18"
tag: 18
Interface "vlan18"
type: internal
Port "vlan2"
tag: 2
Interface "vlan2"
type: internal
Port "bond0"
Interface "eth0"
Interface "eth1"
Port "vlan21"
tag: 21
Interface "vlan21"
type: internal
Port "vmbr0"
Interface "vmbr0"
type: internal
Port "tap20101i2"
tag: 101
Interface "tap20101i2"
Port "tap20101i1"
tag: 100
Interface "tap20101i1"
Port "ln_vnet4040"
tag: 4040
Interface "ln_vnet4040"
type: internal
Port "vlan23"
tag: 23
Interface "vlan23"
type: internal
Port "tap21001i0"
Interface "tap21001i0"
Port "vlan20"
tag: 20
Interface "vlan20"
type: internal
Port "tap21001i1"
Interface "tap21001i1"
Port "vlan1"
Interface "vlan1"
type: internal
Port "tap20101i4"
tag: 103
Interface "tap20101i4"
Port "tap20101i3"
tag: 102
Interface "tap20101i3"
Port "tap20101i0"
tag: 4
Interface "tap20101i0"
ovs_version: "2.12.0"
root@pve00:~# brctl show
bridge name bridge id STP enabled interfaces
vnet4040 8000.aaa8a3efbbb9 no ln_vnet4040
tap20101i5
root@pve00:~# ovs-vsctl list-ports switch_c | xargs -n1 ip link show | grep mtu | column -t
ovs-vsctl: no bridge named switch_c
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN mode DEFAULT group default qlen 1000
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 9000 qdisc mq master ovs-system state UP mode DEFAULT group default qlen 1000
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 9000 qdisc mq master ovs-system state UP mode DEFAULT group default qlen 1000
4: ovs-system: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN mode DEFAULT group default qlen 1000
5: vmbr0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 9000 qdisc noqueue state UNKNOWN mode DEFAULT group default qlen 1000
6: vlan1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 9000 qdisc noqueue state UNKNOWN mode DEFAULT group default qlen 1000
7: vlan18: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 9000 qdisc noqueue state UNKNOWN mode DEFAULT group default qlen 1000
8: vlan20: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 9000 qdisc noqueue state UNKNOWN mode DEFAULT group default qlen 1000
9: vlan21: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 9000 qdisc noqueue state UNKNOWN mode DEFAULT group default qlen 1000
10: vlan23: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 9000 qdisc noqueue state UNKNOWN mode DEFAULT group default qlen 1000
11: vlan2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 9000 qdisc noqueue state UNKNOWN mode DEFAULT group default qlen 1000
12: bond0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UNKNOWN mode DEFAULT group default qlen 1000
13: ln_vnet4040: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master vnet4040 state UNKNOWN mode DEFAULT group default qlen 1000
14: vnet4040: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 9000 qdisc noqueue state UP mode DEFAULT group default qlen 1000
15: tap20101i0: <BROADCAST,MULTICAST,PROMISC,UP,LOWER_UP> mtu 9000 qdisc pfifo_fast master ovs-system state UNKNOWN mode DEFAULT group default qlen 1000
16: tap20101i1: <BROADCAST,MULTICAST,PROMISC,UP,LOWER_UP> mtu 9000 qdisc pfifo_fast master ovs-system state UNKNOWN mode DEFAULT group default qlen 1000
17: tap20101i2: <BROADCAST,MULTICAST,PROMISC,UP,LOWER_UP> mtu 9000 qdisc pfifo_fast master ovs-system state UNKNOWN mode DEFAULT group default qlen 1000
18: tap20101i3: <BROADCAST,MULTICAST,PROMISC,UP,LOWER_UP> mtu 9000 qdisc pfifo_fast master ovs-system state UNKNOWN mode DEFAULT group default qlen 1000
19: tap20101i4: <BROADCAST,MULTICAST,PROMISC,UP,LOWER_UP> mtu 9000 qdisc pfifo_fast master ovs-system state UNKNOWN mode DEFAULT group default qlen 1000
20: tap20101i5: <BROADCAST,MULTICAST,PROMISC,UP,LOWER_UP> mtu 9000 qdisc pfifo_fast master vnet4040 state UNKNOWN mode DEFAULT group default qlen 1000
21: tap21001i0: <BROADCAST,MULTICAST,PROMISC,UP,LOWER_UP> mtu 9000 qdisc mq master ovs-system state UNKNOWN mode DEFAULT group default qlen 1000
22: tap21001i1: <BROADCAST,MULTICAST,PROMISC,UP,LOWER_UP> mtu 9000 qdisc mq master ovs-system state UNKNOWN mode DEFAULT group default qlen 1000