Hello,
in previous post i made lots of assumptions about what could be the reason of random kernel panics. i decided to make a new thread as the previous one started to grow with unneeded information.
now i'm sure its up to iptables. if i dont run it on 2 of my proxmox machines, it runs fine. if i load the iptables with simple rules set it crashes
with kernel panic (a pic also included)
versions:
nic on both servers are integrated. on first - there is intel 2port 1g card on second - hp 2port 1g card.
and i should surely add a notice, that with 2.6.32-4 everything works fine!
and my iptables conf
in previous post i made lots of assumptions about what could be the reason of random kernel panics. i decided to make a new thread as the previous one started to grow with unneeded information.
now i'm sure its up to iptables. if i dont run it on 2 of my proxmox machines, it runs fine. if i load the iptables with simple rules set it crashes
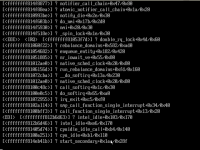
with kernel panic (a pic also included)
Code:
kernel:Kernel panic - not syncing: stack-protector: Kernel stack is corrupted in: ffffffff8149c55c
versions:
Code:
pve-manager: 1.9-24 (pve-manager/1.9/6542)
running kernel: 2.6.32-6-pve
proxmox-ve-2.6.32: 1.9-43
pve-kernel-2.6.32-4-pve: 2.6.32-33
pve-kernel-2.6.32-6-pve: 2.6.32-43
qemu-server: 1.1-32
pve-firmware: 1.0-14
libpve-storage-perl: 1.0-19
vncterm: 0.9-2
vzctl: 3.0.29-1pve1
vzdump: 1.2-16
vzprocps: 2.0.11-2
vzquota: 3.0.11-1
pve-qemu-kvm: 0.15.0-1
ksm-control-daemon: 1.0-6
Code:
Linux services 2.6.32-6-pve #1 SMP Tue Sep 13 10:44:10 CEST 2011 x86_64 GNU/Linuxnic on both servers are integrated. on first - there is intel 2port 1g card on second - hp 2port 1g card.
and i should surely add a notice, that with 2.6.32-4 everything works fine!
and my iptables conf
Code:
services:~# cat /etc/fw
#!/bin/sh
iptables -P INPUT ACCEPT
iptables -P FORWARD ACCEPT
iptables -P OUTPUT ACCEPT
modprobe ipt_REJECT
modprobe ip_conntrack
modprobe ip_conntrack_ftp
my=178.21.xxx.xxx/28
my2=178.21.xxx.xxx/28
barix=178.21.xxx.xxx
tlulib=193.40.xxx.xxx
#flush all rules
iptables -F; iptables -F -t nat; iptables -F -t mangle
#allow everuthing on the loopback interface
iptables -A INPUT -i lo -j ACCEPT
iptables -A OUTPUT -o lo -j ACCEPT
#allow from tower prefix
iptables -A INPUT -s $my -j ACCEPT
iptables -A INPUT -s $tlulib -j ACCEPT
iptables -A INPUT -s $my2 -j ACCEPT
iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
iptables -A INPUT -p icmp -m icmp -j ACCEPT
iptables -A INPUT -j REJECT --reject-with icmp-host-prohibited
#forward (Firewall for VPSes)
ns1=178.21.xxx.xxx
sc1=178.21.xxx.xxx
netflow=178.21.xxx.xxx
noc=178.21.xxx.xxx
ns2=178.21.xxx.xxx
iptables -A FORWARD -p icmp -m icmp -j ACCEPT
iptables -A FORWARD -m state --state ESTABLISHED,RELATED -j ACCEPT
#allow anything from tv tower and tlulib
iptables -A FORWARD -s $my -j ACCEPT
iptables -A FORWARD -s $my2 -j ACCEPT
iptables -A FORWARD -s $tlulib -j ACCEPT
#ns1:
iptables -A FORWARD -d $ns1 -p udp -m udp --dport 53 -j ACCEPT
iptables -A FORWARD -s $ns2 -j ACCEPT
#sc1
#from barix
iptables -A FORWARD -s $barix -j ACCEPT
#for listeners
iptables -A FORWARD -d $sc1 -p tcp -m tcp --dport 8128 -j ACCEPT
iptables -A FORWARD -d $sc1 -p tcp -m tcp --dport 8064 -j ACCEPT
#noc
iptables -A FORWARD -d $noc -p tcp -m tcp --dport 80 -j ACCEPT
iptables -A FORWARD -j REJECT --reject-with icmp-host-prohibited
iptables -nL -v
Last edited: