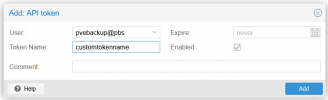
From the documentation:
When trying to connect using the API token the client fails:
Connecting using the username and password without token works fine.
Tried with ZSH and BASH. Both fail.
The API token should be correct since it was just created and permission granted to the user.
Is this a syntax error or what am I doing wrong?
Thanks!
| user@pbs!token@host:store | user@pbs!token | myhostname:8007 | mydatastore |
Bash:
proxmox-backup-client backup server1.pxar:/ --repository 'vmbackup@pbs!MYTOKEN@PBSHOST:backup'When trying to connect using the API token the client fails:
Bash:
Error: error building client for repository vmbackup@pbs!MYTOKEN@PBSHOST:8007:backup - API token secret must be provided!Connecting using the username and password without token works fine.
Tried with ZSH and BASH. Both fail.
The API token should be correct since it was just created and permission granted to the user.
Is this a syntax error or what am I doing wrong?
Thanks!