Hello!
I noticed a weird behaviour regarding firewall rules with my OPNsense VM, where i don't know what is causing it and wheter it's a problem or not.
I'm trying to setup a DMZ (virtually, with a bridge) in addition to LAN and WAN interfaces (both physical; 3 in total but one for the proxmox host itself), and followed tutorials found online.
At first i tried it with OPNsense installed bare metal (on a different computer with 4 physical NICs). After setting up the interface and DHCP in OPNsense, the only thing left to do ist setting a firewall rule allowing all traffic coming from the DMZ-Net with destination "any BUT LAN-Net", according to tutorials. It worked perfectly well and i had internet connectivity and could not access LAN or OPNsense itself.
But then with Proxmox it is somehow not working like that. I have to set an additional rule, allowing traffic from the DMZ-Net to the LAN-Address respectively "This Firewall".
I tried it with bridging two NICs into the OPNsense-VM and a i tried it with PCI passthrough, but same result. And i also tried to turn of the firewall-settings in proxmox for the OPNsense-VM and a Ubuntu-CT, which i bridged with the DMZ for testing. So somehow it needs a connection to 192.168.1.1 (OPNsense/LAN), which it doesn't need bare-metal.
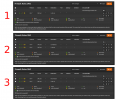
I attached a picture summarizing my problem; (1) only working on bare-metal, but not on proxmox, (2) and (3) working on proxmox.
I hope somebody can clarify things for me, if i'm doing something wrong or this is normal?
Thanks and BR
I noticed a weird behaviour regarding firewall rules with my OPNsense VM, where i don't know what is causing it and wheter it's a problem or not.
I'm trying to setup a DMZ (virtually, with a bridge) in addition to LAN and WAN interfaces (both physical; 3 in total but one for the proxmox host itself), and followed tutorials found online.
At first i tried it with OPNsense installed bare metal (on a different computer with 4 physical NICs). After setting up the interface and DHCP in OPNsense, the only thing left to do ist setting a firewall rule allowing all traffic coming from the DMZ-Net with destination "any BUT LAN-Net", according to tutorials. It worked perfectly well and i had internet connectivity and could not access LAN or OPNsense itself.
But then with Proxmox it is somehow not working like that. I have to set an additional rule, allowing traffic from the DMZ-Net to the LAN-Address respectively "This Firewall".
I tried it with bridging two NICs into the OPNsense-VM and a i tried it with PCI passthrough, but same result. And i also tried to turn of the firewall-settings in proxmox for the OPNsense-VM and a Ubuntu-CT, which i bridged with the DMZ for testing. So somehow it needs a connection to 192.168.1.1 (OPNsense/LAN), which it doesn't need bare-metal.
I attached a picture summarizing my problem; (1) only working on bare-metal, but not on proxmox, (2) and (3) working on proxmox.
I hope somebody can clarify things for me, if i'm doing something wrong or this is normal?
Thanks and BR