Hello all,
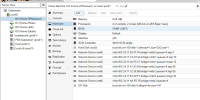
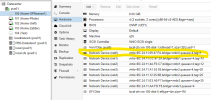
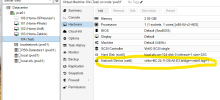
I have built an OPNsense VM on my Proxmox 8.2.7 server. The VM has a LAN and WAN side. I have also built a simple Ubuntu desktop VM, so I could configure the OPNsense VM via its GUI. I cannot ping the OPNsense VM from the Ubuntu desktop and vice versa. Both VMs are on the same vmbr/vlan on the Proxmox server. Both have manual IP configs. I even took it one more step and made the gateway of the Ubuntu desktop the IP of the OPNsense VM LAN side.
I don't know Proxmox as well as I do VMware. Does Proxmox have a virtual switch similar to VMware? Do I need to configure anything, so that both VMs can ping each other? Has anyone been able to get an OPNsense VM to work?
Thanks,
Steve
I have built an OPNsense VM on my Proxmox 8.2.7 server. The VM has a LAN and WAN side. I have also built a simple Ubuntu desktop VM, so I could configure the OPNsense VM via its GUI. I cannot ping the OPNsense VM from the Ubuntu desktop and vice versa. Both VMs are on the same vmbr/vlan on the Proxmox server. Both have manual IP configs. I even took it one more step and made the gateway of the Ubuntu desktop the IP of the OPNsense VM LAN side.
I don't know Proxmox as well as I do VMware. Does Proxmox have a virtual switch similar to VMware? Do I need to configure anything, so that both VMs can ping each other? Has anyone been able to get an OPNsense VM to work?
Thanks,
Steve