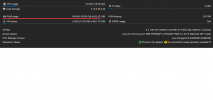
Sep 09 18:40:27 nuc11propve kernel: systemd-journal invoked oom-killer: gfp_mask=0x140cca(GFP_HIGHUSER_MOVABLE|__GFP_COMP), order=0, oom_score_adj=-250
Sep 09 18:40:27 nuc11propve kernel: CPU: 5 PID: 1856820 Comm: systemd-journal Tainted: P O 6.2.16-10-pve #1
Sep 09 18:40:27 nuc11propve kernel: Hardware name: Intel(R) Client Systems NUC11TNHv5/NUC11TNBv5, BIOS TNTGLV57.0074.2023.0705.1856 07/05/2023
Sep 09 18:40:27 nuc11propve kernel: Call Trace:
Sep 09 18:40:27 nuc11propve kernel: <TASK>
Sep 09 18:40:27 nuc11propve kernel: dump_stack_lvl+0x48/0x70
Sep 09 18:40:27 nuc11propve kernel: dump_stack+0x10/0x20
Sep 09 18:40:27 nuc11propve kernel: dump_header+0x50/0x290
Sep 09 18:40:27 nuc11propve kernel: oom_kill_process+0x10d/0x1c0
Sep 09 18:40:27 nuc11propve kernel: out_of_memory+0x23c/0x570
Sep 09 18:40:27 nuc11propve kernel: __alloc_pages+0x1180/0x13a0
Sep 09 18:40:28 nuc11propve kernel: ? rrw_exit+0x72/0x170 [zfs]
Sep 09 18:40:28 nuc11propve kernel: alloc_pages+0x90/0x1a0
Sep 09 18:40:28 nuc11propve kernel: folio_alloc+0x1d/0x60
Sep 09 18:40:28 nuc11propve kernel: filemap_alloc_folio+0xfd/0x110
Sep 09 18:40:28 nuc11propve kernel: __filemap_get_folio+0x1d4/0x3c0
Sep 09 18:40:28 nuc11propve kernel: filemap_fault+0x14a/0x940
Sep 09 18:40:28 nuc11propve kernel: ? filemap_map_pages+0x14b/0x6f0
Sep 09 18:40:28 nuc11propve kernel: __do_fault+0x36/0x150
Sep 09 18:40:28 nuc11propve kernel: do_fault+0x1c7/0x430
Sep 09 18:40:28 nuc11propve kernel: __handle_mm_fault+0x6d9/0x1070
Sep 09 18:40:28 nuc11propve kernel: handle_mm_fault+0x119/0x330
Sep 09 18:40:28 nuc11propve kernel: ? lock_mm_and_find_vma+0x43/0x230
Sep 09 18:40:28 nuc11propve kernel: do_user_addr_fault+0x194/0x620
Sep 09 18:40:28 nuc11propve kernel: exc_page_fault+0x80/0x1b0
Sep 09 18:40:28 nuc11propve kernel: asm_exc_page_fault+0x27/0x30
Sep 09 18:40:28 nuc11propve kernel: RIP: 0033:0x7fadf5cf23a0
Sep 09 18:40:28 nuc11propve kernel: Code: Unable to access opcode bytes at 0x7fadf5cf2376.
Sep 09 18:40:28 nuc11propve kernel: RSP: 002b:00007ffd93e22cd8 EFLAGS: 00010202
Sep 09 18:40:28 nuc11propve kernel: RAX: 0000000000000007 RBX: 000055a0aef8dd20 RCX: 00007fadf5d69780
Sep 09 18:40:28 nuc11propve kernel: RDX: 0000000000000001 RSI: 0000000000000007 RDI: 000055a0aef8dd20
Sep 09 18:40:28 nuc11propve kernel: RBP: 000055a0aef7dbc0 R08: 00000000000000a7 R09: 0000000006758900
Sep 09 18:40:29 nuc11propve kernel: R10: 0000000000000000 R11: 0000000000000000 R12: 0000000000000007
Sep 09 18:40:29 nuc11propve kernel: R13: 0000000000218420 R14: 0000000000000000 R15: 00007ffd93e22d00
Sep 09 18:40:29 nuc11propve kernel: </TASK>
Sep 09 18:40:29 nuc11propve kernel: Mem-Info:
Sep 09 18:40:29 nuc11propve kernel: active_anon:6812440 inactive_anon:736168 isolated_anon:0
active_file:2170 inactive_file:2100 isolated_file:3
unevictable:46 dirty:132 writeback:360
slab_reclaimable:111802 slab_unreclaimable:2808331
mapped:26809 shmem:92999 pagetables:21159
sec_pagetables:14533 bounce:0
kernel_misc_reclaimable:0
free:123875 free_pcp:251 free_cma:0