You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
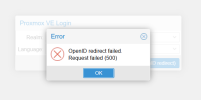
Did you configure custom ports (80/443) in Authentik?
Otherwise your Issuer URL is missing the ports (9000 for http, 9443 for https by default).
I've set up Authentik here for testing, and so far it seems to work as long as you specify a username claim (e.g. username) instead of using the default. The default runs into a `user name too long` error since it uses `sub` as default claim.
But that results in a different error.
Otherwise your Issuer URL is missing the ports (9000 for http, 9443 for https by default).
I've set up Authentik here for testing, and so far it seems to work as long as you specify a username claim (e.g. username) instead of using the default. The default runs into a `user name too long` error since it uses `sub` as default claim.
But that results in a different error.
I use port 444 for HTTPS since I'm running authentik in a docker container. I tried adding 444 to the issuer URL but still got the same issue.Did you configure custom ports (80/443) in Authentik?
Otherwise your Issuer URL is missing the ports (9000 for http, 9443 for https by default).
I've set up Authentik here for testing, and so far it seems to work as long as you specify a username claim (e.g. username) instead of using the default. The default runs into a `user name too long` error since it uses `sub` as default claim.
But that results in a different error.
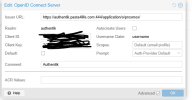
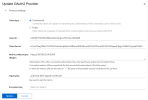
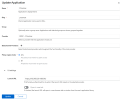
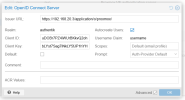
Here's my authentik config:
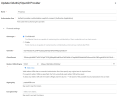
I changed my cert in Authentik to match my wildcart cert for the domain. I also added this as a custom cert to Proxmox.
Attachments
No, sorry.Do you know what the header configuration requirements are for this?
But I'm pretty sure someone else already configured it and provided details about their setup. This should not be limited to just PVE, but probably similar/the same for other setups as well, as long as an OpenID Connect provider is used.
Howdy all,
I also experienced the same issue when using self-signed SSL certs. I believe the issue is that the Proxmox internals are refusing to connect to the self-signed https endpoint due to not trusting the SSL cert.
TL;DR: Use a trusted SSL cert (or tell Proxmox to trust the CA which signed the SSL cert)
If you cannot obtain one, then create a CA; create an SSL cert signed by that CA for use by your IdP; add the CA to the trusted CAs used by Debian/Proxmox.
This site gives instructions on how to do this: https://arminreiter.com/2022/01/create-your-own-certificate-authority-ca-using-openssl/
Note that the CA does not need to be created on the Proxmox host, but it must be added to the CA store of Proxmox.
The certificate of the IdP must be signed by a CA and cannot be signed by itself. I tried adding the self-signed cert to the CA store and it did not work.
I hope this helps, please let me know if y'all have questions.
Grace and Peace,
William
I also experienced the same issue when using self-signed SSL certs. I believe the issue is that the Proxmox internals are refusing to connect to the self-signed https endpoint due to not trusting the SSL cert.
TL;DR: Use a trusted SSL cert (or tell Proxmox to trust the CA which signed the SSL cert)
If you cannot obtain one, then create a CA; create an SSL cert signed by that CA for use by your IdP; add the CA to the trusted CAs used by Debian/Proxmox.
This site gives instructions on how to do this: https://arminreiter.com/2022/01/create-your-own-certificate-authority-ca-using-openssl/
Note that the CA does not need to be created on the Proxmox host, but it must be added to the CA store of Proxmox.
The certificate of the IdP must be signed by a CA and cannot be signed by itself. I tried adding the self-signed cert to the CA store and it did not work.
I hope this helps, please let me know if y'all have questions.
Grace and Peace,
William