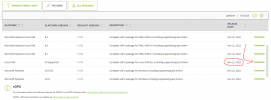
Hi all,
recently we got access to a vGPU capable GPU (RTX A5000), and we put together a short how-to on how to use it with a current PVE 7.x here:
https://pve.proxmox.com/wiki/NVIDIA_vGPU_on_Proxmox_VE_7.x
While Proxmox VE is not a supported platform for NVIDIAs GRID/vGPU, it seems to work quite well here. There are some things in the wiki article that are not fully packaged yet, but those are denoted by their upcoming versions.
Also note that there are more improvements incoming for handling pci passthrough (especially for clusters) (see [0] for the current state)
which will make using vgpus even easier (i will update the wiki article when those patches will be applied)
If you have any questions or suggestions, just ask here.
0: https://lists.proxmox.com/pipermail/pve-devel/2022-July/053565.html
recently we got access to a vGPU capable GPU (RTX A5000), and we put together a short how-to on how to use it with a current PVE 7.x here:
https://pve.proxmox.com/wiki/NVIDIA_vGPU_on_Proxmox_VE_7.x
While Proxmox VE is not a supported platform for NVIDIAs GRID/vGPU, it seems to work quite well here. There are some things in the wiki article that are not fully packaged yet, but those are denoted by their upcoming versions.
Also note that there are more improvements incoming for handling pci passthrough (especially for clusters) (see [0] for the current state)
which will make using vgpus even easier (i will update the wiki article when those patches will be applied)
If you have any questions or suggestions, just ask here.
0: https://lists.proxmox.com/pipermail/pve-devel/2022-July/053565.html