I've set my system up to use NAT. Which works ok, I can give my containers network access and run services on them
However I am currently just running one bridge for the network and extending that with new pre and post iptables routes for each port on each container I want to expose.
The problem is, when you add a new container, you need to bump the bridge to load the new config. Which disconnects all the other containers. Which is a bit of a pain
Is there a more flexible way of doing this.
My thought was to create a bridge with a small subnet range, like a /28 for a bridge. Assign each container a bridge. Then when I want to restart the network for that container I only impact that container.
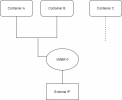
This is my example
Where I have my bond0 setup.
vmbr0 is the first NATed bridge I created as I mentioned.
Then I have my pre and post routing firewall rules for some of my containers. Which as you can see gets a bit unwieldy
so I created vmbr1 as an additional bridge. This one worked partially. I can bring the bridge up and connect to this from the proxmox command line. However when I tried to ssh to this one, ssh wouldn't make a connection to it.
Dont know if I need to make a new zone . i.e.
post-up iptables -t raw -I PREROUTING -i fwbr+ -j CT --zone 2
post-down iptables -t raw -D PREROUTING -i fwbr+ -j CT --zone 2
Any help would be ideal
However I am currently just running one bridge for the network and extending that with new pre and post iptables routes for each port on each container I want to expose.
The problem is, when you add a new container, you need to bump the bridge to load the new config. Which disconnects all the other containers. Which is a bit of a pain
Is there a more flexible way of doing this.
My thought was to create a bridge with a small subnet range, like a /28 for a bridge. Assign each container a bridge. Then when I want to restart the network for that container I only impact that container.
This is my example
auto enp6s0
iface enp6s0 inet manual
auto enp7s0
iface enp7s0 inet manual
iface enp8s0 inet manual
iface enp9s0 inet manual
auto bond0
iface bond0 inet static
address 10.126.24.82/24
gateway 10.126.24.1
bond-slaves enp6s0 enp7s0
bond-miimon 100
bond-mode 802.3ad
bond-xmit-hash-policy layer2+3
auto vmbr0
iface vmbr0 inet static
address 192.168.10.14/28
bridge-ports none
bridge-stp off
bridge-fd 0
post-up echo 1 > /proc/sys/net/ipv4/ip_forward
post-up iptables -t nat -A POSTROUTING -s 192.168.10.0/28 -o bond0 -j MASQUERADE
post-down iptables -t nat -D POSTROUTING -s 192.168.10.0/28 -o bond0 -j MASQUERADE
post-up iptables -t raw -I PREROUTING -i fwbr+ -j CT --zone 1
post-down iptables -t raw -D PREROUTING -i fwbr+ -j CT --zone 1
post-up iptables -t nat -A PREROUTING -p tcp --dport 2212 -j DNAT --to-destination 192.168.10.2:22
post-down iptables -t nat -A PREROUTING -p tcp --dport 2212 -j DNAT --to-destination 192.168.10.2:22
post-up iptables -t nat -A POSTROUTING -p tcp --sport 22 -s 192.168.10.2 -j SNAT --to-source 192.168.10.14:2212
post-down iptables -t nat -A POSTROUTING -p tcp --sport 22 -s 192.168.10.2 -j SNAT --to-source 192.168.10.14:2212
post-up iptables -t nat -A PREROUTING -p tcp --dport 2210 -j DNAT --to-destination 192.168.10.3:22
post-down iptables -t nat -A PREROUTING -p tcp --dport 2210 -j DNAT --to-destination 192.168.10.3:22
post-up iptables -t nat -A POSTROUTING -p tcp --sport 22 -s 192.168.10.3 -j SNAT --to-source 192.168.10.14:2210
post-down iptables -t nat -A POSTROUTING -p tcp --sport 22 -s 192.168.10.3 -j SNAT --to-source 192.168.10.14:2210
post-up iptables -t nat -A PREROUTING -p tcp --dport 8010 -j DNAT --to-destination 192.168.10.3:80
post-down iptables -t nat -A PREROUTING -p tcp --dport 8010 -j DNAT --to-destination 192.168.10.3:80
post-up iptables -t nat -A PREROUTING -p tcp --sport 80 -j DNAT --to-destination 192.168.10.14:8010
post-down iptables -t nat -A PREROUTING -p tcp --sport 80 -j DNAT --to-destination 192.168.10.14:8010
post-up iptables -t nat -A PREROUTING -p tcp --dport 2211 -j DNAT --to-destination 192.168.10.10:22
post-down iptables -t nat -A PREROUTING -p tcp --dport 2211 -j DNAT --to-destination 192.168.10.10:22
post-up iptables -t nat -A POSTROUTING -p tcp --sport 22 -s 192.168.10.10 -j SNAT --to-source 192.168.10.14:2211
post-down iptables -t nat -A POSTROUTING -p tcp --sport 22 -s 192.168.10.10 -j SNAT --to-source 192.168.10.14:2211
auto vmbr1
iface vmbr1 inet static
address 192.168.10.16/28
bridge-ports none
bridge-stp off
bridge-fd 0
bridge-vlan-aware yes
bridge-vids 2-4094
post-up echo 1 > /proc/sys/net/ipv4/ip_forward
post-up iptables -t nat -A POSTROUTING -s 192.168.10.16/28 -o bond0 -j MASQUERADE
post-down iptables -t nat -D POSTROUTING -s 192.168.10.16/28 -o bond0 -j MASQUERADE
post-up iptables -t raw -I PREROUTING -i fwbr+ -j CT --zone 1
post-down iptables -t raw -D PREROUTING -i fwbr+ -j CT --zone 1
post-up iptables -t nat -A PREROUTING -p tcp --dport 2214 -j DNAT --to-destination 192.168.10.17:22
post-down iptables -t nat -A PREROUTING -p tcp --dport 2214 -j DNAT --to-destination 192.168.10.17:22
post-up iptables -t nat -A POSTROUTING -p tcp --sport 22 -s 192.168.10.17 -j SNAT --to-source 192.168.10.16:2214
post-down iptables -t nat -A POSTROUTING -p tcp --sport 22 -s 192.168.10.17 -j SNAT --to-source 192.168.10.16:2214
Where I have my bond0 setup.
vmbr0 is the first NATed bridge I created as I mentioned.
Then I have my pre and post routing firewall rules for some of my containers. Which as you can see gets a bit unwieldy
so I created vmbr1 as an additional bridge. This one worked partially. I can bring the bridge up and connect to this from the proxmox command line. However when I tried to ssh to this one, ssh wouldn't make a connection to it.
Dont know if I need to make a new zone . i.e.
post-up iptables -t raw -I PREROUTING -i fwbr+ -j CT --zone 2
post-down iptables -t raw -D PREROUTING -i fwbr+ -j CT --zone 2
Any help would be ideal