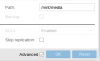
I am trying to mount a host LVM to multiple unprivileged containers but having little luck. Here is the relevant parts of my unprivileged container conf file.
What I have done:
Created a uid/gid on the HOST and CONTAINER for app-files (1005)
And SUBGID/SUBUID respectively
But when I start the container, the shared mount is inaccessible.
Help!
What I have done:
Created a uid/gid on the HOST and CONTAINER for app-files (1005)
Code:
mp0: local-lvm:vm-108-disk-3,mp=/mnt/MYDIR
lxc.idmap = u 0 100000 1005
lxc.idmap = g 0 100000 1005
lxc.idmap = u 1005 1005 1
lxc.idmap = g 1005 1005 1
lxc.idmap = u 1006 101006 64530
lxc.idmap = g 1006 101006 64530And SUBGID/SUBUID respectively
Code:
root@prox:/etc/pve/lxc# cat /etc/subgid
root:1005:1
root:100000:65536
systemd-timesync:100000:65536
systemd-network:165536:65536
systemd-resolve:231072:65536
systemd-bus-proxy:296608:65536
statd:362144:65536
sshd:427680:65536
messagebus:493216:65536
postfix:558752:65536
ais:624288:65536
app-files:689824:65536
Code:
root@prox:/etc/pve/lxc# cat /etc/subuid
root:1005:1
root:100000:65536
systemd-timesync:100000:65536
systemd-network:165536:65536
systemd-resolve:231072:65536
systemd-bus-proxy:296608:65536
statd:362144:65536
sshd:427680:65536
messagebus:493216:65536
postfix:558752:65536
ais:624288:65536
app-files:689824:65536But when I start the container, the shared mount is inaccessible.
Code:
root@container:~# ls -l /mnt
total 184
drwxrwx--- 10 nobody nogroup 188416 Jun 29 18:47 MYDIRHelp!