Hi,
I have a problem receiving emails from a small number of servers, no emails make it through and i get the following message in the syslog:
After some investigation I think this is down to PMG sending out the old root certificate for Letsencrypt. CheckTLS.com shows that it is sending it as seen here:
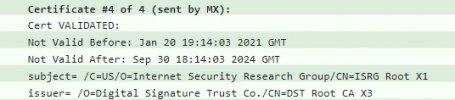
I understand the DST Root CA X3 certificate has expired, and some older systems don't handle it correctly, but I don't know how to prevent PMG from sending it. I do need to be able to receive from at least one of the servers that is not able to connect, however trying to talk to the server owner has proved to be not possible.
Please advise if I'm going down the right path here, and if so what can be done.
Many thanks.
I have a problem receiving emails from a small number of servers, no emails make it through and i get the following message in the syslog:
Code:
warning: TLS library problem: error:14094415:SSL routines:ssl3_read_bytes:sslv3 alert certificate expired:../ssl/record/rec_layer_s3.c:1543:SSL alert number 45After some investigation I think this is down to PMG sending out the old root certificate for Letsencrypt. CheckTLS.com shows that it is sending it as seen here:

I understand the DST Root CA X3 certificate has expired, and some older systems don't handle it correctly, but I don't know how to prevent PMG from sending it. I do need to be able to receive from at least one of the servers that is not able to connect, however trying to talk to the server owner has proved to be not possible.
Please advise if I'm going down the right path here, and if so what can be done.
Many thanks.

