Hello!
I've been following this guide from Craft Computing on Youtube to create a Bazzite gaming VM that I can access remotely.
He includes a link to this cheatsheet for passing through a GPU to the Bazzite VM.
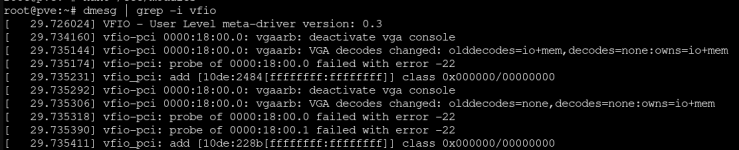
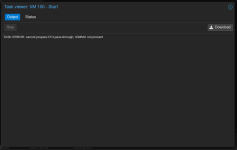
I've followed the guide meticulously for my Dell RTX 3070, but I get this error when I try to start the VM:
This is the output of
: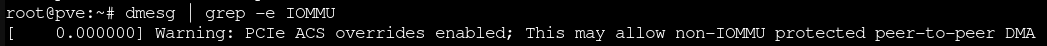
**This forum post validated that output as correct/expected after using the recommendation for the /etc/default/grub config file.
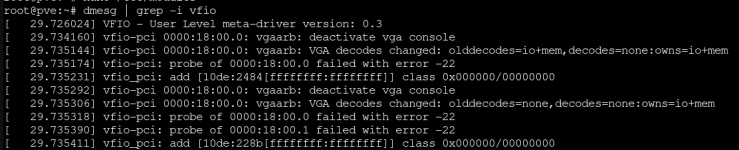
This is the output of
:
I'm at a loss as to how to fix this. I've verified that I'm using grub to boot and Intel Virtualization capabilities are enabled in the BIOS.
This is a new build on a Dell Precision 7820 with Dual Xeon 6146 Gold CPUs and I'm trying to pass through an NVIDIA RTX 3070.
Any input on where to look next would be appreciated!
I've been following this guide from Craft Computing on Youtube to create a Bazzite gaming VM that I can access remotely.
He includes a link to this cheatsheet for passing through a GPU to the Bazzite VM.
I've followed the guide meticulously for my Dell RTX 3070, but I get this error when I try to start the VM:

This is the output of
Code:
dmesg | grep -e IOMMU**This forum post validated that output as correct/expected after using the recommendation for the /etc/default/grub config file.
This is the output of
Code:
dmesg | grep -i vfio
I'm at a loss as to how to fix this. I've verified that I'm using grub to boot and Intel Virtualization capabilities are enabled in the BIOS.
This is a new build on a Dell Precision 7820 with Dual Xeon 6146 Gold CPUs and I'm trying to pass through an NVIDIA RTX 3070.
Any input on where to look next would be appreciated!