Hey, I've been fighting with trying to get OpenID connect working with Proxmox VE 7 for a little while now and I was wondering if anyone could lend me some insight into my issue here.
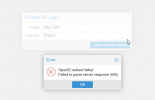
After setting up my OpenID authentication backen/realm on both proxmox and Gluu (my IDP server) I get the following error when I click the redirect button on login.
Any help or insights would be appreciated! Thank you.
Some relevant logs and configuration hopefully:
Access log for login attempt:
Browser network tool, response:
Gluu Server config (Known to work with other OpenID implementations):
After setting up my OpenID authentication backen/realm on both proxmox and Gluu (my IDP server) I get the following error when I click the redirect button on login.
Any help or insights would be appreciated! Thank you.

Some relevant logs and configuration hopefully:
Code:
root@pve01:/etc/pve# cat domains.cfg
openid: gluu
comment Gluu SSO
client-id YYYYYYYYYYYYY
issuer-url https://sso.<DOMAIN>.com
client-key XXXXXXXXXXX
default 0
username-claim username
pve: pve
comment Proxmox VE authentication server
pam: pam
comment Linux PAM standard authentication
Code:
/var/log/pveproxy# tail -f access.log
::ffff:10.0.10.1 - - [24/07/2021:21:39:39 -0500] "GET /pve2/ext6/theme-crisp/resources/theme-crisp-all.css HTTP/1.1" 200 66
::ffff:10.0.10.1 - - [24/07/2021:21:39:40 -0500] "GET /api2/json/access/domains HTTP/1.1" 200 213
::ffff:10.0.10.1 - - [24/07/2021:21:39:45 -0500] "POST /api2/extjs/access/openid/auth-url HTTP/1.1" 200 84
::ffff:10.0.10.1 - - [24/07/2021:21:39:45 -0500] "GET /pve2/ext6/theme-crisp/resources/images/tools/tool-sprites.png HTTP/1.1" 200 24404
Code:
https://<PVE_URL>/api2/extjs/access/openid/auth-url
{"message":"Failed to parse server response\n","data":null,"success":0,"status":500}
Code:
OPENID CONNECT CLIENTS DETAILS
------------------------------
- **Name:** Proxmox
- **Description:** Hypervisor
- **Client ID:** YYYYYYYYYYYYY
- **Subject Type:** pairwise
- **Expirattion date:** Sat Jan 01 00:00:00 UTC 2146
- **ClientSecret:** XXXXXXXXXXX
- **Application Type:** web
- **Persist Client Authorizations:** true
- **Pre-Authorization:** false
- **Authentication method for the Token Endpoint:** client_secret_post
- **Logout Session Required:** false
- **Include Claims In Id Token:** false
- **Disabled:** false
- **Login Redirect URIs:** [https://<PVE_URL>/]
- **Scopes:** [openid, email, user_name]
- **Grant types:** [refresh_token]
- **Response types:** [code]
