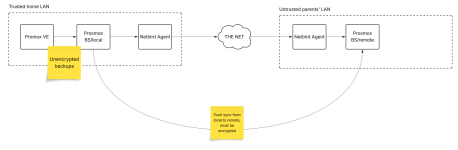
I currently run a Proxmox PVE and PBS in my home environment, both on their own physical machines. While this is great for the mandatory on-site backup, it doesn't help with natural disasters and such, so I really want to add an off-site solution. Luckily, my parents just got really fast fiber internet, and they would let me put a bit of hardware in their basement.
My plan for this would be simple: Buy a UGreen DXP-4800+, put PBS and Netbird on it and sync my local PBS to that machine. There is a problem though: I don't have any influence on physical security at my parent's home and I wouldn't even dream of storing an unencrypted backup there.
My initial, naive assumption was that Proxmox PBS will surely support some kind of encrypted remote for syncing. Well, I do now know that this is a case where the Anakin/Padme meme fits really well. Synced remote backups can only be encrypted if the original local backup was encrypted. Which is a well-hidden feature in Proxmox PVE (i.e. not exposed on the GUI), and I also conciously chose not to use it because the official documentation clearly advises against it in a pure local trusted network situation like mine...
Now, I wil probably do something really ugly like putting a restic REST server on that NAS and then use restic to put an encrypted backup of my datastore there. This is really clumsy because restic's retention policy overlaps with that of PBS and it's a pure command line adventure, but well, it will work. Somehow. I hope.
So here is my plea to the developers: Please add an optional encryption key for push sync jobs. It obviously makes little sense for pull syncs as we want the key to reside on the trusted side, but it would probably be quite trivial to add to the push sync. And please, don't do this in a way that requires shell access and isn't exposed on the GUI. I suffer from heavy ADHD, and having to remember that there's something on the shell that I have to keep in mind is a major obstacle for me.
My plan for this would be simple: Buy a UGreen DXP-4800+, put PBS and Netbird on it and sync my local PBS to that machine. There is a problem though: I don't have any influence on physical security at my parent's home and I wouldn't even dream of storing an unencrypted backup there.
My initial, naive assumption was that Proxmox PBS will surely support some kind of encrypted remote for syncing. Well, I do now know that this is a case where the Anakin/Padme meme fits really well. Synced remote backups can only be encrypted if the original local backup was encrypted. Which is a well-hidden feature in Proxmox PVE (i.e. not exposed on the GUI), and I also conciously chose not to use it because the official documentation clearly advises against it in a pure local trusted network situation like mine...
Now, I wil probably do something really ugly like putting a restic REST server on that NAS and then use restic to put an encrypted backup of my datastore there. This is really clumsy because restic's retention policy overlaps with that of PBS and it's a pure command line adventure, but well, it will work. Somehow. I hope.
So here is my plea to the developers: Please add an optional encryption key for push sync jobs. It obviously makes little sense for pull syncs as we want the key to reside on the trusted side, but it would probably be quite trivial to add to the push sync. And please, don't do this in a way that requires shell access and isn't exposed on the GUI. I suffer from heavy ADHD, and having to remember that there's something on the shell that I have to keep in mind is a major obstacle for me.