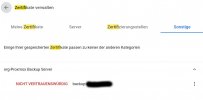
I get a ssl certificate error on login to a newly installed pbs backup server.
Added a new DDNS name on dynu.net added this to pve acme setup and can order both certificates for pve (which works fine via https) and new for pbs.
I don’t know how to setup it on actual pbs server.
Any clues are appreciated!
Thx
Added a new DDNS name on dynu.net added this to pve acme setup and can order both certificates for pve (which works fine via https) and new for pbs.
I don’t know how to setup it on actual pbs server.
Any clues are appreciated!
Thx