I can see in the API documentation where the endpoint is for creating an authentication ticket:
https://pmg.proxmox.com/pmg-docs/api-viewer/index.html#/access/ticket
I don't see anything in the main documentation describing how to use the REST API.
I have provided the username and password which are correct and accepted. The response is JSON which includes a key "NeedTFA" = "1". I see that there is another key "otp" which can be included in the POST. When I set that otp value to the TOTP displayed currently, the response is a 401 authentication failure. I have also tried one of the backup codes as the value in the otp field.
What am I doing incorrectly here? And is there basic API docs to read?
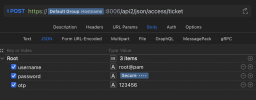
https://pmg.proxmox.com/pmg-docs/api-viewer/index.html#/access/ticket
I don't see anything in the main documentation describing how to use the REST API.
I have provided the username and password which are correct and accepted. The response is JSON which includes a key "NeedTFA" = "1". I see that there is another key "otp" which can be included in the POST. When I set that otp value to the TOTP displayed currently, the response is a 401 authentication failure. I have also tried one of the backup codes as the value in the otp field.
What am I doing incorrectly here? And is there basic API docs to read?


