Hi,
I was not able find on step by step tutorial on setting up the LDAP authentication for FreeIPA so I am writing this guide for someone like me who is unable to find the guide for this. Please feel free to add anything that I am missing.
Step 1: Go to Datacenter -> Realms -> Add -> LDAP Server
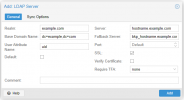
Step2: Fill the "General" section with the following details
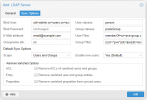
Step3: Fill the Sync Options with the following details and Click "Add"
Step4: Now select the added Realm and click the "Sync" button. With the below options press Sync.

Once the sync is pressed the Proxmox users and groups will automatically synchronized from the FreeIPA LDAP server. You can check the user and group details in the Users and Groups tab.
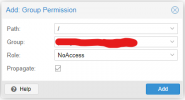
Step5: Setup the related group/user permissions in the permissions tab.
Step6: Once you are sure that above steps are working as expected add the below line to chron jobs in the server to synchronize the Users and Groups automatically.
Reference Links:
I was not able find on step by step tutorial on setting up the LDAP authentication for FreeIPA so I am writing this guide for someone like me who is unable to find the guide for this. Please feel free to add anything that I am missing.
Step 1: Go to Datacenter -> Realms -> Add -> LDAP Server
Step2: Fill the "General" section with the following details
- Realm: example.com
- Server: hostname.example.com
- Base Domain Name: dc=example,dc=com
- Fallback Server (Optional): bkp_hostname.example.com
- User Attribute Name: uid
- Port: Default
- SSL: Checked
- Verify Certificate: Unchecked
- Require TFA: none

Step3: Fill the Sync Options with the following details and Click "Add"
- Bind User: uid=admin,cn=users,cn=accounts,dc=example,dc=com
- Bind Password: Password
- Email Attribute(Optional): email@example.com
- Groupname attr.: cn
- User Classes: person
- Group Classes: posixGroup
- User Filter: memberOf=cn=pve-group,cn=groups,cn=accounts,dc=example,dc=com
- Group Filter: (|(cn=*pve*)(dc=ipa)(dc=example)(dc=com))
- Scope: Users and Groups
- Enable new users: Yes
- ACL: Checked
- Entry: Checked
- Properties: Checked

Step4: Now select the added Realm and click the "Sync" button. With the below options press Sync.
- Scope: Users and Groups
- Enable new: Yes
- ACL: Checked
- Entry: Checked
- Properties: Checked

Once the sync is pressed the Proxmox users and groups will automatically synchronized from the FreeIPA LDAP server. You can check the user and group details in the Users and Groups tab.
Step5: Setup the related group/user permissions in the permissions tab.

Step6: Once you are sure that above steps are working as expected add the below line to chron jobs in the server to synchronize the Users and Groups automatically.
*/15 * * * * pveum realm sync example.com > /var/log/ldap-sync.logReference Links:
Last edited:

